Lemon_Duck cryptomining botnet targets Docker servers
Security Affairs
APRIL 22, 2022
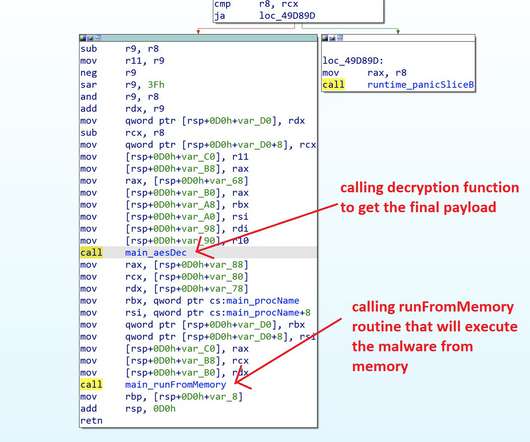
The Lemon_Duck cryptomining botnet is targeting Docker servers to mine cryptocurrency on Linux systems. Crowdstrikes researchers reported that the Lemon_Duck cryptomining botnet is targeting Docker to mine cryptocurrency on Linux systems. “The “a.asp” file is the actual payload in this attack. ” concludes the report.












































Let's personalize your content