CISA adds JBoss RichFaces Framework flaw to its Known Exploited Vulnerabilities catalog
Security Affairs
SEPTEMBER 28, 2023
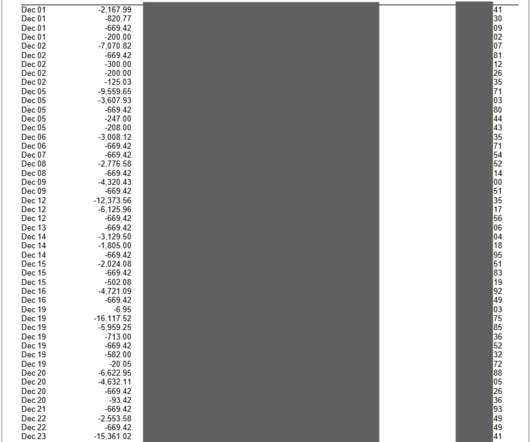
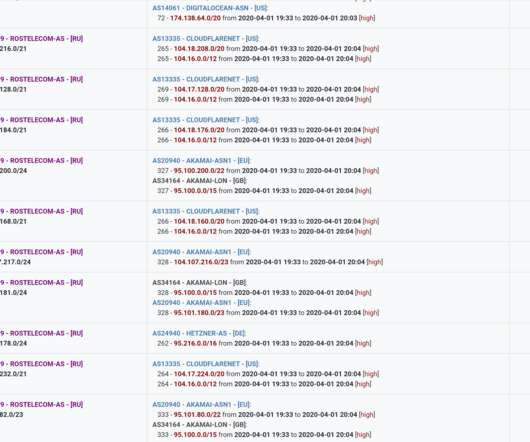
US CISA added the flaw CVE-2018-14667 in Red Hat JBoss RichFaces Framework to its Known Exploited Vulnerabilities catalog. US Cybersecurity and Infrastructure Security Agency (CISA) added the critical flaw CVE-2018-14667 (CVSS score 9.8) affecting Red Hat JBoss RichFaces Framework to its Known Exploited Vulnerabilities Catalog.












































Let's personalize your content