New Linux variant of BIFROSE RAT uses deceptive domain strategies
Security Affairs
MARCH 3, 2024
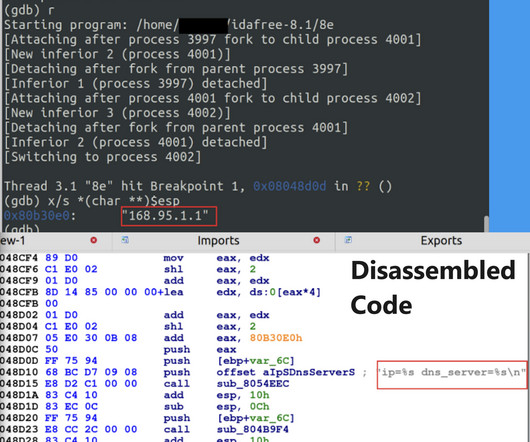
The Bifrost RAT has been active since 2004, it allows its operators to gather sensitive information, including hostname and IP address. ” reads the analysis published by Unit 42. ” The sample binary analyzed by the experts is compiled for x86, the authors removed debugging information and symbol tables to hinder analysis.



































Let's personalize your content