Behind the Scenes: Providing Access to Supreme Court Oral Arguments
Unwritten Record
MARCH 15, 2024
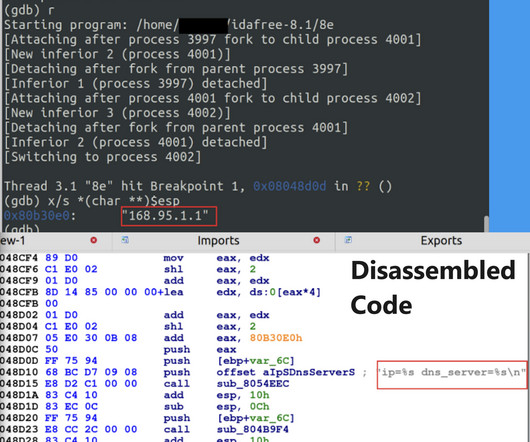
The Catalog can now facilitate access to searching, listening to, and downloading digital audio files of oral arguments and opinion announcements, as recorded by the Court from 1955 to 2022. For many years thereafter, he worked directly with NARA staff to further NARA’s preservation and access goals for the Supreme Court audio recordings.












































Let's personalize your content