The iPhone 11 Pro’s Location Data Puzzler
Krebs on Security
DECEMBER 4, 2019
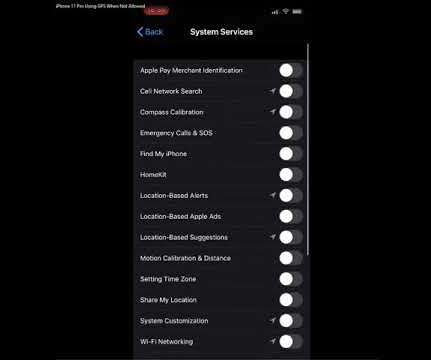
x, sharing a video showing how the device still seeks the user’s location when each app and system service is set to “never” request location information (but with the main Location Data service still turned on). The video above was recorded on a brand new iPhone 11 Pro. on iPhone 11 Pro devices.


























Let's personalize your content