Leaking Military Secrets on Gaming Discussion Boards
Schneier on Security
JUNE 8, 2022
People are leaking classified military information on discussion boards for the video game War Thunder to win arguments — repeatedly.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Schneier on Security
JUNE 8, 2022
People are leaking classified military information on discussion boards for the video game War Thunder to win arguments — repeatedly.

The Last Watchdog
OCTOBER 10, 2023
As tragic as it is, we are in a space where video has become a crucial asset in wartime. Related: Apple tool used as warfare weapon Ukraine’s defense against Russian invaders has changed the role of video. Metadata’s role As important as the video content itself is, there is an even more critical element: metadata.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
FEBRUARY 28, 2020
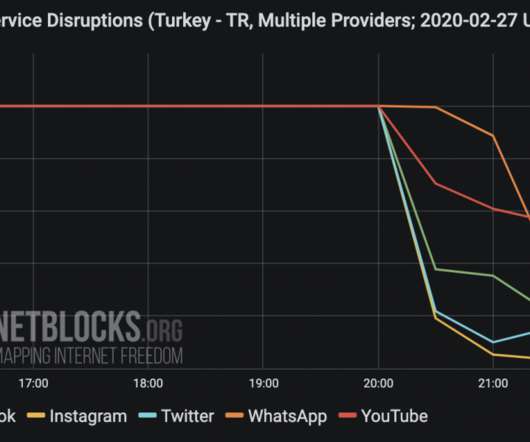
Network data collected by the NetBlocks internet observatory confirm that Turkey has blocked access to social media as Idlib military crisis escalates. In December 2016 , the Turkish blocked social media in the country to prevent the sharing of a video of the executions of Turkish soldiers by the IS group. ”added Netblocks. .

Unwritten Record
JUNE 23, 2022
Archival films and videos can help bring your NHD topic alive, allowing your audience to engage with and understand historical events in exciting ways. Whether or not your documentary focuses on a filmed event, videos downloaded from the National Archives Catalog can help weave a rich tapestry of images for your viewers. Documentary.
Data Breach Today
JANUARY 9, 2020
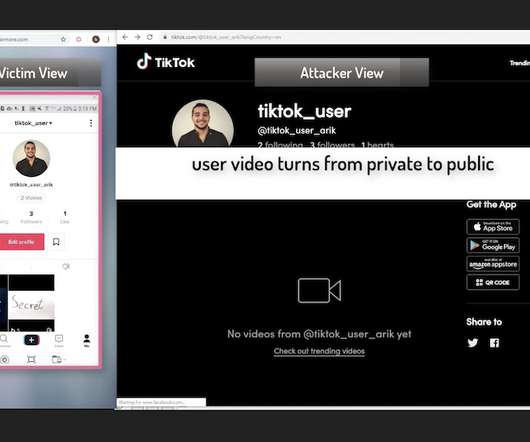
Now Fixed, Check Point Says Flaws Could Have Led to Account Takeover The security company Check Point has revealed several vulnerabilities in TikTok, the popular Chinese video app that has raised concerns lately from the U.S. military and lawmakers.
Krebs on Security
FEBRUARY 28, 2024
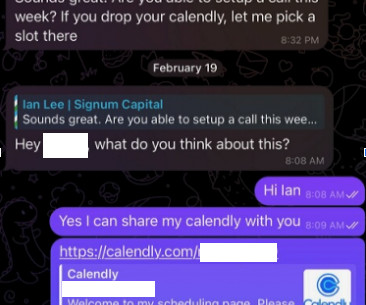
The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. The investor expressed interest in financially supporting Doug’s startup, and asked if Doug could find time for a video call to discuss investment prospects. “We are actively working on fixing these problems. .

Security Affairs
JUNE 18, 2020
Security researchers at ESET recently uncovered a campaign carried out by the InvisiMole group that has been targeting a small number of high-profile organizations in the military sector and diplomatic missions in Eastern Europe. The SMInit exploit chain exploits a vulnerability in the legitimate Total Video Player software.

Schneier on Security
JANUARY 24, 2019
Considering the storage capacity of microSD memory cards, a pigeon's organic characteristics provide front line forces a relatively clandestine mean to transport gigabytes of video, voice, or still imagery and documentation over considerable distance with zero electromagnetic emissions or obvious detectability to radar.
Security Affairs
APRIL 15, 2024
The Blackjack group is believed to be affiliated with Ukrainian intelligence services that carried out other attacks against Russian targets, including an internet provider and a military infrastructure. YouTube Video 1 , YouTube Video 2 ). All servers have been deleted.

Security Affairs
JANUARY 2, 2024
Source Radio Free Europe website The Record Media, citing an investigation by Radio Free Europe, reported that Russia’s spies gained access to video footage from thousands of surveillance cameras in Ukraine that used a Russian software known as Trassir.
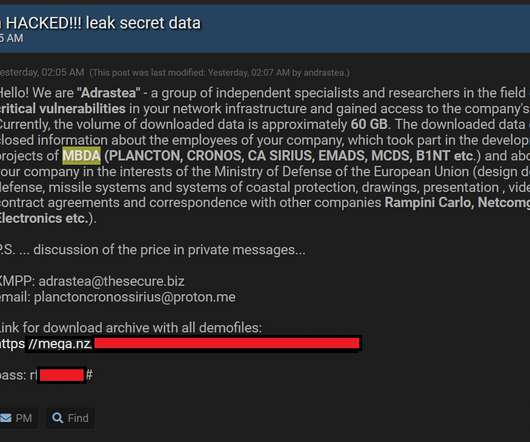
Security Affairs
JULY 31, 2022
The attackers said that the stolen data includes information about the employees of the company involved in military projects, commercial activities, contract agreements and correspondence with other companies. Adrastea said that they have found critical vulnerabilities in the company infrastructure and have stolen 60 GB of confidential data.

Security Affairs
MARCH 10, 2024
Judge ordered NSO Group to hand over the Pegasus spyware code to WhatsApp Cybercrime BlackCat Ransomware Affiliate TTPs American Express credit cards EXPOSED in third-party vendor data breach – account numbers and names among details accessed in hack LockBit 3.0’S

Security Affairs
JULY 17, 2020
Iran-linked APT35 group accidentally exposed one of its servers, leaving online roughly 40 GB of videos and other files associated with its operations. The experts found several files on the server, roughly five hours of training videos recorded by the APT group. Some of the videos were showing how to exfiltrate data (i.e.

The Security Ledger
FEBRUARY 21, 2024
Related Stories BitCoins To Bombs: North Korea Funds Military With Billions In Stolen Cryptocurrency China Calls Out U.S. Video Podcast ] | [ MP3 ] | [ Transcript ] Four years ago, I sat down with Gary McGraw in the Security Ledger studio to talk about a report released by his new project, The Berryville Institute of Machine learning.

Security Affairs
JANUARY 29, 2023
Copycat Criminals mimicking Lockbit gang in northern Europe Sandworm APT targets Ukraine with new SwiftSlicer wiper ISC fixed high-severity flaws in DNS software suite BIND Patch management is crucial to protect Exchange servers, Microsoft warns Hacker accused of having stolen personal data of all Austrians and more CVE-2023-23560 flaw exposes 100 (..)

Schneier on Security
AUGUST 27, 2018
military would be unable to respond effectively for a while. Years of worry about a possible Chinese "Assassin's Mace" -- a silver bullet super-weapon capable of disabling key parts of the American military -- turned out to be focused on the wrong thing. Finally, it had, though the U.S.

Data Protection Report
AUGUST 20, 2021
Please click here for a video-on-demand link to our recent webinar providing an overview of the data security and protection regime in China. Personal information involving more than 100,000 individuals; and.
Security Affairs
AUGUST 23, 2020
The Transparent Tribe cyber-espionage group continues to improve its arsenal while targets Military and Government entities. The Transparent Tribe APT group is carrying out an ongoing cyberespionage campaign aimed at military and diplomatic targets worldwide. Transparent Tribe continues to show high activity against multiple targets.

Unwritten Record
NOVEMBER 17, 2020
The International Military Tribunal , more commonly known at the Nuremberg trials , began this week 75 years ago in Nuremberg, Germany. The trials were a series of military tribunals held to convict major Nazi German leaders on charges of crimes against peace, war crimes, crimes against humanity, and conspiracy to commit each of these crimes.

Security Affairs
FEBRUARY 28, 2021
During a video conference of the members of the European Council, EU leaders agreed on a new strategy aimed at boosting defense and security. “The EU efforts are going hand in hand with the military efforts across the continent,” said Stoltenberg. ” said Charles Michel, President of the European Council.

The Last Watchdog
APRIL 22, 2019
The Boulder, CO-based company got its start in the mid-1990s as a pioneer of massive multi-player video games. Skelly Suddenly, cybersecurity training comes across as a lot more appealing, especially for the next generation of cyber warriors who grew up immersed in video games. “By

Unwritten Record
NOVEMBER 8, 2021
The records of the military branches are a particularly plentiful source of material, with footage from the 1921 ceremony through the early 21st century. These films were created to document visits to the Tomb by military officials, diplomats, and U.S. Clip from “Youth Visits Our Nation’s Capital” ( 119.3 ).

The Last Watchdog
DECEMBER 3, 2023
Related: Big data can foster improved healthcare Within that, video represents over 80 percent of the traffic that flows through this global network which is growing rapidly at about 25 percent per year. A tremendous amount of video traffic is being managed by IT departments.

Security Affairs
OCTOBER 1, 2023
million newborns and pregnancy care patients Xenomorph malware is back after months of hiatus and expands the list of targets Smishing Triad Stretches Its Tentacles into the United Arab Emirates Crooks stole $200 million worth of assets from Mixin Network A phishing campaign targets Ukrainian military entities with drone manual lures Alert!

Security Affairs
DECEMBER 14, 2023
Federal Bureau of Investigation (FBI), National Security Agency (NSA), Polish Military Counterintelligence Service (SKW), CERT Polska (CERT.PL), and the UK’s National Cyber Security Centre (NCSC) the group is targeting TeamCity servers since September 2023. The flaw impacts on-premises version 2023.05.3

Unwritten Record
APRIL 13, 2021
1945 (NAID 5768, Local Identifier 18-SFP) (313 new item descriptions with scanned catalog cards; 11 video files). 1936 (NAID 24608, Local Identifier 111-H) (video files and scanned production files added to 450 existing item descriptions). 1965 (NAID 607018, Local Identifier 306-IN) (350 new item descriptions with 273 video files).

Adam Levin
DECEMBER 18, 2018
The report makes several recommendations to mitigate the systemic vulnerabilities, most of them widely recognized best cybersecurity practices including multi-factor authentication, increased video surveillance at facilities, securing server racks and placing tighter controls on removable media such as USB keys.

Security Affairs
AUGUST 6, 2019
The STRONTIUM APT group (aka APT28 , Fancy Bear , Pawn Storm , Sofacy Group , and Sednit ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election. ” concludes Microsoft.

Security Affairs
AUGUST 23, 2019
The SBU seized equipment composed of two metal cases containing that included coolers and video cards ( Radeon RX 470 GPU), computer components commonly used in mining factories. ” reported ZDnet.

The Security Ledger
JULY 31, 2018
There is more alarming security news for consumers with smart devices at home: hackers can take remote control of video cameras, thermostats, smart locks or other IoT devices by exploiting vulnerabilities discovered in Samsung’s SmartThings Hub, according to a report by Cisco Systems’ Talos research group. Cisco Talos researchers.

The Security Ledger
NOVEMBER 21, 2023
and other militaries have always been at the top of the target list for so-called “advanced persistent threat” cyber adversaries. In fact, the term “advanced persistent threat” (or APT) was concocted by U.S.

The Last Watchdog
MAY 13, 2020
Thanks to the sudden rise in use of Zoom and other video conferencing systems by an expanding work-from-home workforce, their logons are begin targeted by threat actors; underground forums today are bristling with databases holding hundreds of thousands of recycled Zoom logon credentials.

Security Affairs
AUGUST 14, 2020
The problem was first reported by Bleepingcomputer, which tracked a suspicious outage on Canon’s image.canon cloud photo and video storage service. The memo also reveals that the company has hired an external security firm to investigate the incident.

The Security Ledger
JANUARY 23, 2024
Software is now central to the operation of our economy – as digital transformation washes over every industry.

eSecurity Planet
JULY 20, 2023
Mitnick often represented the company at conferences and discussed his experience in KnowBe4 training videos. military systems and launch nuclear missiles through mere whistling. He helped design KnowBe4’s training based on his social engineering tactics, and he became a partial owner of KnowBe4 in November 2011.
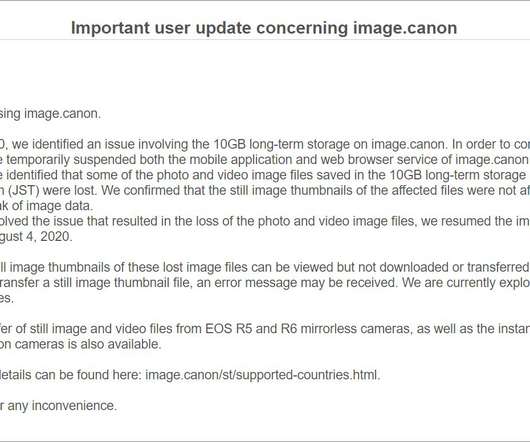
Security Affairs
AUGUST 7, 2020
The problem was first reported by Bleepingcomputer, which tracked a suspicious outage on Canon’s image.canon cloud photo and video storage service. The memo also reveals that the company has hired an external security firm to investigate the incident.

Security Affairs
APRIL 22, 2021
The popular cryptographer and researcher Moxie claims the list of customers of the company includes authoritarian regimes in Belarus, Russia, Venezuela, and China, death squads in Bangladesh, and military juntas in Myanmar. Cellebrite produce two primary pieces products, the UFED and Physical Analyzer.

Security Affairs
JUNE 19, 2019
The attackers appear to be focused o n stealing military-related information. Attackers distributed the malware in tainted legitimate applications that are hosted on websites advertised on social media. .”

Preservica
MARCH 7, 2022
Military Women’s Memorial - The nonprofit organization is the only historical repository documenting a century of stories from all military women's service. Watch this 2-minute video to learn more. View the entire record without accessing Twitter or downloading software.

Troy Hunt
JULY 13, 2018
Polar Fitness and military personnel tracking. Your static website needs HTTPS (I kinda love this video, it was fun and the feedback has been sensational ). True story: this was a corporate mandate in my last job as we were going through a round of layoffs!). References. Domain Factory in Germany. Timehop got popped.

Unwritten Record
MARCH 11, 2021
We preserve more than half a million reels of film and hundreds of thousands of sound and video recordings made by federal agencies. Moving Images and the Military. The National Archives and Records Administration is the archival repository of the United States government. Government and the People. Public Diplomacy.

Thales Cloud Protection & Licensing
SEPTEMBER 12, 2019
First, it said that it would invest in cultivating military assets in the digital space, as reported by the Organization for World Peace. For more information on this, read Satellite Navigation on the Rugby Field and watch this video on GeoNav IoT, A Secure GeoNav Solution.

The Security Ledger
NOVEMBER 11, 2019
» Related Stories From China with Love: New York Firm sold millions in PRC Surveillance Gear to US Government, Military Episode 165: Oh, Canada! We're joined by Terry Dunlap the co-founder of ReFirm Labs to talk about why software supply chain risks. Read the whole entry. » Also: Breaking Bad Security Habits.

Data Matters
JUNE 16, 2021
semiconductor production, scientific research, development of artificial intelligence, and space exploration in the face of growing economic, technological, and military competition from China. Senate adopted by a 68-32 vote S. Senate Majority Leader Charles Schumer, D-N.Y., The bipartisan bill, sponsored by Sens. Maria Cantwell, D-Wash.,
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content