Google announces V8 Sandbox to protect Chrome users
Security Affairs
APRIL 9, 2024
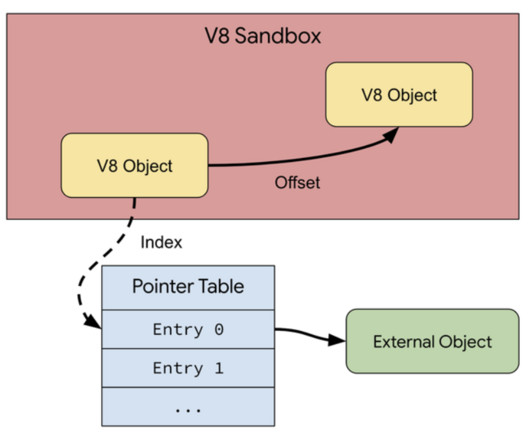
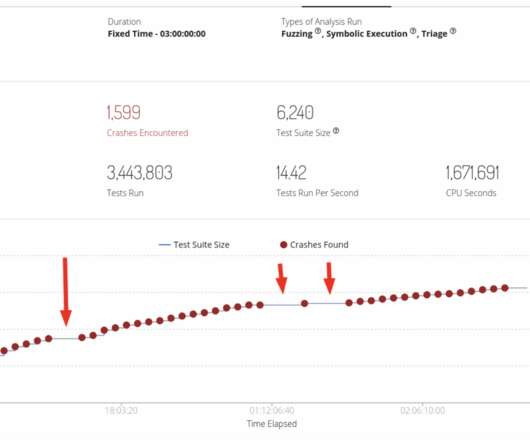
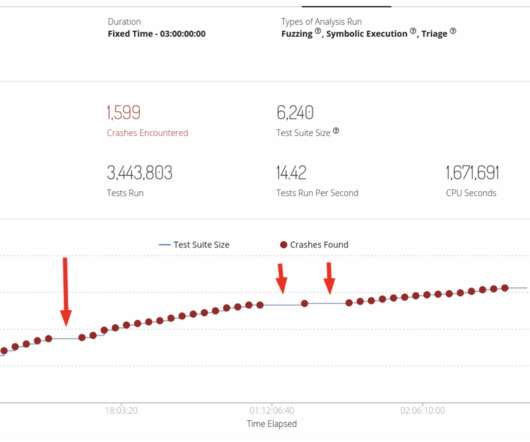
Google announced support for a V8 Sandbox in the Chrome web browser to protect users from exploits triggering memory corruption issues. Chrome 123 is a sort of “beta” release for the sandbox designed to mitigate memory corruption issues in the Javascript engine. ” reads the announcement.












































Let's personalize your content