Are Retailers Shopping for a Cybersecurity Breach?
Thales Cloud Protection & Licensing
NOVEMBER 22, 2022
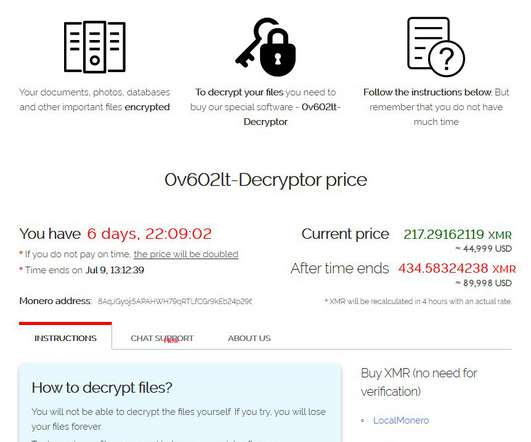
Are Retailers Shopping for a Cybersecurity Breach? Retailers started the century as the prime targets for cyber attackers looking for credit card data. Today, unfortunately, retailers are again coming back to the spotlight. Similar to many organizations, 36% of retail respondents cited human error as the leading threat.













































Let's personalize your content