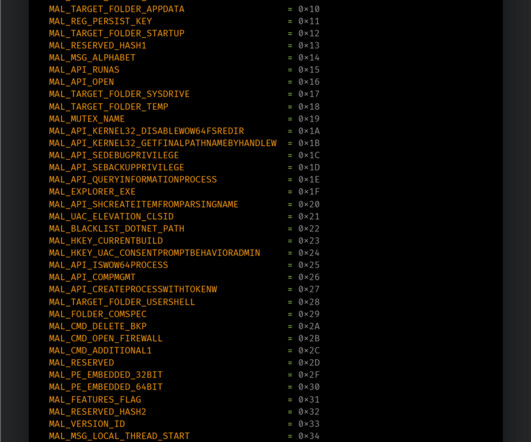
8Base ransomware operators use a new variant of the Phobos ransomware
Security Affairs
NOVEMBER 19, 2023
The group has been active since March 2022, it focused on small and medium-size businesses in multiple industries, including finance, manufacturing, business services, and IT. Security experts attributed 67 attacks to the group in May 2023, most of the victims are in the U.S. and Brazil. ” reads the report published by Talos.”Once










































Let's personalize your content