Feds Seize LockBit Ransomware Websites, Offer Decryption Tools, Troll Affiliates
Krebs on Security
FEBRUARY 20, 2024
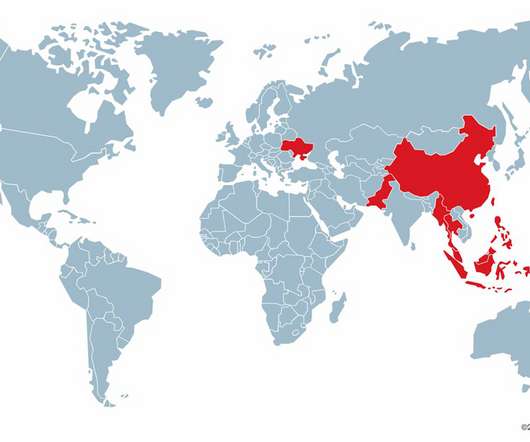
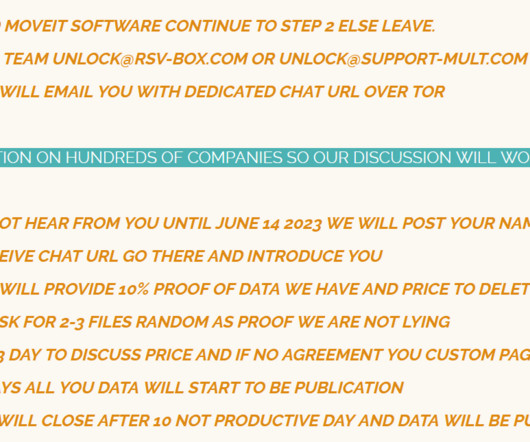
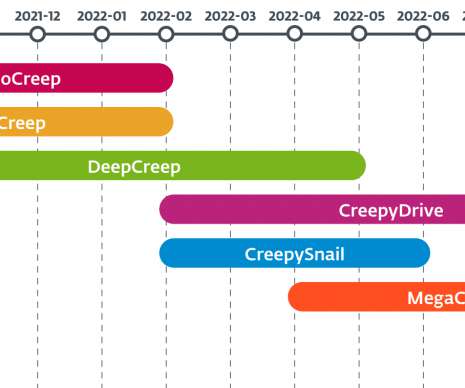
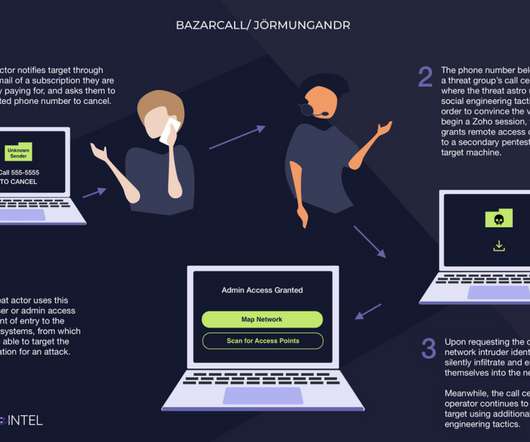
authorities have seized the darknet websites run by LockBit , a prolific and destructive ransomware group that has claimed more than 2,000 victims worldwide and extorted over $120 million in payments. Investigators used the existing design on LockBit’s victim shaming website to feature press releases and free decryption tools.
















































Let's personalize your content