Global Data Breaches and Cyber Attacks in March 2024 – 299,368,075 Records Breached
IT Governance
APRIL 4, 2024
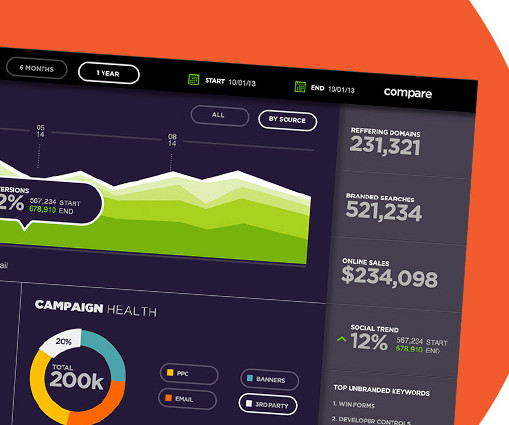
This is largely caused by two outlier events: Misconfigured Google Firebase instances , exposing 124,605,664 records across 916 misconfigured websites. To minimise data skewing, we’ve accounted for this by providing two Data Breach Dashboards this month: one including and one excluding the above events.















































Let's personalize your content