Jamf Event: Education recap
Jamf
APRIL 9, 2024
The 2024 Jamf Event showed how to transform learning for students, teachers and parents; better protect students; and maintain seamless, secure access.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Jamf
APRIL 9, 2024
The 2024 Jamf Event showed how to transform learning for students, teachers and parents; better protect students; and maintain seamless, secure access.

Dark Reading
JUNE 10, 2022
Cisco's TK Keanini and the NFL's Tomás Maldonado join Dark Reading's Terry Sweeney at Dark Reading News Desk during RSA Conference to talk about end-to-end security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
AUGUST 3, 2022
Also: Latest Analysis of Log 4j Event; How to Secure Evolving Work Patterns John Kindervag, creator of zero trust and senior vice president at ON2IT, and Grant Schneider, senior director at Venable, join ISMG editors to discuss the latest Log 4j findings, threats posed by a Chinese-made automotive GPS tracker and the challenges of a distributed workforce. (..)

IT Governance
APRIL 24, 2024
Previously , I had the pleasure of sitting down with Sophie Sayer, our Channel Sales Director, to talk about the IT Governance partner programme and partner event on 9 April 2024. When I asked her how the event went, she said: The Channel Partner Event and Awards 2024 in Ely was an absolute triumph!

Thales Cloud Protection & Licensing
OCTOBER 5, 2022
Global October Cybersecurity Events: Where You Can Find Thales. The summer is now over, and October is a month full of cybersecurity events for Thales around the world. Below are just some of the events Thales will be at over the next few weeks. Les Assises turns 22 this year, and the event motto is "In 2022, We Speed Up!"

IBM Big Data Hub
JANUARY 8, 2024
In modern enterprises, where operations leave a massive digital footprint, business events allow companies to become more adaptable and able to recognize and respond to opportunities or threats as they occur. Teams want more visibility and access to events so they can reuse and innovate on the work of others.

eSecurity Planet
MAY 10, 2022
Hackers have found a way to infect Windows Event Logs with fileless malware , security researchers have found. During a “very targeted” campaign, hackers used Windows Event Logs to inject shellcode payloads and operate stealthily. How the Attackers Injected Code in Windows Logs. How to Protect Against Event Log Attacks.

IBM Big Data Hub
NOVEMBER 10, 2023
This blog will focus on the integration of IBM Cloud Code Engine and IBM Cloud Event Notifications along with IBM Cloud Secrets Manager to build a robust use case that will automate your certificate renewal process for applications in your code engine project. What is IBM Cloud Event Notifications? What is IBM Cloud Secrets Manager?

Security Affairs
MAY 27, 2022
Security researchers devised a technique, dubbed GhostTouch, to remotely control touchscreens using electromagnetic signals. The researchers demonstrated how to inject two types of basic touch events, taps and swipes, into targeted locations of the touchscreen. The events allowed the researchers to control the devices (i.e.

IBM Big Data Hub
APRIL 24, 2024
They are also vulnerable to prompt injections , a significant security flaw with no apparent fix. Cybersecurity best practices Many of the same security measures organizations use to protect the rest of their networks can strengthen defenses against prompt injections. Say a field on a web form asks for a user’s US phone number.

IBM Big Data Hub
JANUARY 22, 2024
The good news is that in the event of a ransomware attack, there are basic steps any organization can follow to help contain the attack, protect sensitive information, and ensure business continuity by minimizing downtime. Notify the security team Once you’ve disconnected the affected systems, notify your IT security team of the attack.

IBM Big Data Hub
JANUARY 19, 2024
Disaster recovery strategies provide the framework for team members to get a business back up and running after an unplanned event. Like DRPs, BCPs and IRPs are both parts of a larger disaster recovery strategy that a business can rely on to help restore normal operations in the event of a disaster.

ForAllSecure
MAY 4, 2023
We participated in B Sides last month, hosted a webinar on “How to Increase Test Coverage With Mayhem for API”, and hosted a university hackathon at UC Santa Cruz. Use Open-Source Safely: How to Uncover and Address Vulnerabilities in Open-Source Libraries Open-source libraries can be a double-edged sword for software developers.
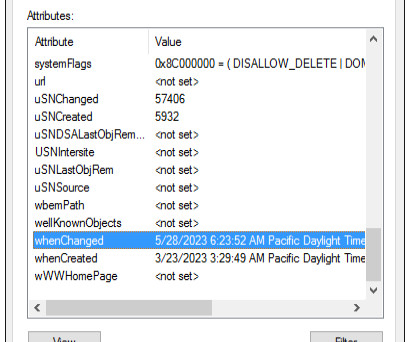
eSecurity Planet
SEPTEMBER 14, 2023
Active Directory is one of the most critically important IT assets and a frequent target of hackers, so securing it is a top priority for IT and security teams. It is possible for an attacker to employ attack strategies that would prevent any events from being recorded in the event logs.

eSecurity Planet
MARCH 18, 2022
Many security professionals think that if they have done the hard work of securing their organization, that should be enough. Even though drafting IT security policies can be a pain, formal policies provide a valuable resource to protect both the IT team and their organization. Written security policies.

IT Governance
OCTOBER 11, 2022
One of the most common mistakes that organisations make when addressing cyber security is that they consider it a one-off event. This process should be embedded within your overall cyber security measures in what experts refer to as cyber defence in depth. What is threat management?

The Last Watchdog
MAY 18, 2023
Related: Fallout of T-Mobile hack Hackers of modest skill routinely bypass legacy security measures, even two-factor authentication, with techniques such as overlay attacks. Many corporations outsource their mobile app development, and these apps often exhibit poor security practices, making them easy targets for cybercriminals, he says.

Thales Cloud Protection & Licensing
NOVEMBER 20, 2022
How to Secure Access for your Seasonal Workers. To cope with the continuous flow of personnel, businesses need to establish a robust and effective Identity and Access Management policy to reduce potential security risks and enable seamless and instant access to digital systems. Mon, 11/21/2022 - 05:36.
ForAllSecure
JUNE 7, 2023
We have 4 upcoming events planned for June 2023: Mayhem Unleashed Webinar: Discover our Next Generation Security Testing Solution DevSecOps Roundtable CyberSecurity Summit Hartford ForAllSecure APFT (Adversary, Penetration, and FuzzTesting) Training Read on to learn more about June’s events. We hope to see you there!

eSecurity Planet
FEBRUARY 21, 2024
A firewall audit is a procedure for reviewing and reconfiguring firewalls as needed so they still suit your organization’s security goals. A firewall audit is a thorough procedure that requires your IT and security teams to look closely at your firewall documentation and change management processes. Check firmware, too.

IBM Big Data Hub
JANUARY 11, 2024
Successful business owners know how important it is to have a plan in place for when unexpected events shut down normal operations. Disaster recovery plan (DRP): A disaster recovery plan (DRP) is a document that clearly outlines how an enterprise will recover from an unexpected event.

The Last Watchdog
MAY 8, 2023
And even though people are becoming increasingly aware of the immense possibilities that exists when starting a career in the field, the pace at which they are gaining the required skills and knowledge to meet the security needs of organizations is not as high as the growing demand for their assistance. Try non-traditional channels.

Thales Cloud Protection & Licensing
SEPTEMBER 12, 2019
Sports fans aren’t the only ones who are looking forward to this event. It’s not like bad actors haven’t taken an interest in major sporting events before. Just a couple of months after that, World Rugby itself announced that one of its training websites had suffered a security breach that exposed subscribers’ account information.

Security Affairs
APRIL 30, 2023
Thales cybersecurity researchers have shown this week how they seized control of a European Space Agency (ESA) satellite. Credit: ESA – European Space Agency The offensive cybersecurity team at Thales demonstrated how to take control of the ESA satellite, the is considered the world’s first ethical satellite hacking exercise.

eSecurity Planet
AUGUST 4, 2023
Even a robust IT or security department will find certain tasks or projects beyond their capabilities. But ignoring issues that you lack the time or expertise for can risk operational failure or security incidents. Yet IT and security vendors will provide their services according to the specifics of the contract.

The Last Watchdog
MARCH 29, 2022
Log4j is the latest, greatest vulnerability to demonstrate just how tenuous the security of modern networks has become. By no means has the cybersecurity community been blind to the complex security challenges spinning out of digital transformation. Related: The exposures created by API profileration.

eSecurity Planet
APRIL 18, 2022
Secured computer systems can use advanced detection tools to spot and block such suspicious activities and even catch adversaries. Antivirus and EDR tools, SIEM systems (security information and event management), security vendors, software, hardware, firmware, and operating systems. How to Protect Against Reconnaissance.

eSecurity Planet
OCTOBER 12, 2023
That’s the case with Active Directory legacy protocols, so to help you secure your Active Directory environment, we’ve created a script to help you ensure that legacy protocols are disabled. Your primary goal in securing Active Directory infrastructure is to reduce the attack surface. We explain how to do so below.

IT Governance
FEBRUARY 27, 2020
That means creating a detailed cyber security policy. What is a cyber security policy? A cyber security policy outlines an organisation’s cyber security defence strategy. It’s only by documenting these that you can be sure that your organisation is approaching cyber security comprehensively and efficiently.

eSecurity Planet
DECEMBER 9, 2021
We make IT, security, or any business decision by weighing the risks and the rewards. Or as is often the case with security, what costs can we skip and still escape big penalties later? Dealing with an incident is a matter of “when and how bad,” not “if.” What investments can we make to drive down costs or increase sales?

Thales Cloud Protection & Licensing
JANUARY 28, 2020
An extension of the celebration for Data Protection Day in Europe, Data Privacy Day functions as the signature event of the National Cyber Security Centre’s ongoing education and awareness efforts surrounding online privacy. With the above in mind, it’s worth a discussion about specific security controls in greater detail….

eSecurity Planet
JANUARY 18, 2024
When assessing the overall security of cloud storage and choosing a solution tailored to your business, it helps to determine its features, potential risks, security measures, and other considerations. It excels in remote access, scalability, and security, with distributed storage options and privacy adherence capabilities.

AIIM
MARCH 29, 2022
From the Australian Open offering fans art ball NFTs with real-time match data to JPMorgan Chase’s tiger-friendly lounge in the blockchain-based world Decentraland, metaverse events are exploding into 2022 as powerful new weapons to engage with people. will surely become insurmountable walls. The Metaverse is Coming.

eSecurity Planet
APRIL 30, 2024
Setting up a firewall is the first step in securing your network. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively improve your network integrity and data security. Take note of your security requirements, physical environment, and component interoperability.

IT Governance
AUGUST 1, 2022
You must assemble a team, conduct a gap analysis and risk assessment, apply security controls, create documentation and perform staff awareness training. How to maintain ISO 27001 certification. An ISMS isn’t just about preventing security breaches, though. Promote ongoing information security staff awareness.

eSecurity Planet
AUGUST 22, 2023
And breaches will occur – because bad guys make a living by figuring out ways to circumvent security best practices. Prioritize Data Protection The downfall of many security strategies is that they become too general and too thinly spread. But it requires different levels of security.

eSecurity Planet
JUNE 23, 2023
Scott Lyons, CEO of Red Lion notes, “The value of any test is less about if the pentester can get into the system and much more about if the system can prove its value to the business in resilience, ability to protect the system, or ability to provide alerts to security teams.” “The

IT Governance
APRIL 8, 2020
As a reminder of that, we’re back with more of our experiences and advice on how to manage through the pandemic. We also have a selection of free tools to help you address some of the challenges you’ll face, and summarise the latest coronavirus-related security threats. Cyber attacks. Phishing attacks. Expert advice.

IT Governance
AUGUST 18, 2022
An ISO 27001 internal audit is a thorough examination of an organisation’s ISMS (information security management system) to ensure that: It meets the requirements of ISO 27001; It meets the organisation’s aims and objectives; and The policies, processes and other controls work as intended. What is an ISO 27001 internal audit? Get started.

IBM Big Data Hub
FEBRUARY 23, 2024
The only processing operations exempt from the GDPR are national security and law enforcement activities and purely personal uses of data. Storage limitation: Organizations should securely dispose of data as soon as its purpose is fulfilled. Organizations can also take this opportunity to strengthen data security measures.

The Last Watchdog
AUGUST 18, 2021
Meanwhile, native security is increasingly being built into popular operating systems, and there’s a trend toward beefing up application security, as well. They seem to be attempting to address the consumer security market more holistically, while also expanding their customer base and geographical regions. Mellen: Absolutely.

IBM Big Data Hub
DECEMBER 8, 2023
The only way for effective risk reduction is for an organization to use a step-by-step risk mitigation strategy to sort and manage risk, ensuring the organization has a business continuity plan in place for unexpected events. Contingency plans should be in place if something drastic changes or risk events occur.

eSecurity Planet
MARCH 15, 2021
In an era where the network edge faces the highest traffic, organizations rush to add more robust security yet hesitate to take on the long-term endeavor known as microsegmentation. Instead, by enhancing visibility into how data flows, network administrators can work with business and security analysts to create application enabled policies.

erwin
MARCH 25, 2021
erwin recently hosted the second in its six-part webinar series on the practice of data governance and how to proactively deal with its complexities. Led by Frank Pörschmann of iDIGMA GmbH, an IT industry veteran and data governance strategist, the second webinar focused on “ The Value of Data Governance & How to Quantify It.”.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content