Feds Charge Four Russians With Energy Sector Attacks
Data Breach Today
MARCH 25, 2022
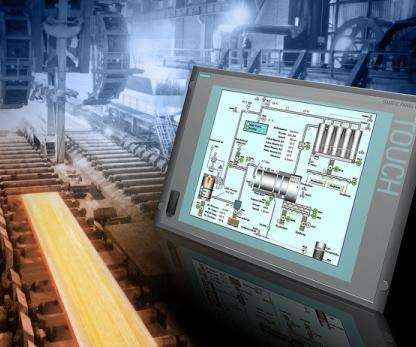
Men Allegedly Targeted Utilities, Nuclear Plants, Oil and Gas Firms The U.S. Department of Justice unsealed two indictments against suspected Russian nation-state actors on conspiracy charges for attacks on the global energy sector. This move comes as the U.S.












































Let's personalize your content