US Government Sites Give Bad Security Advice
Krebs on Security
MARCH 25, 2020
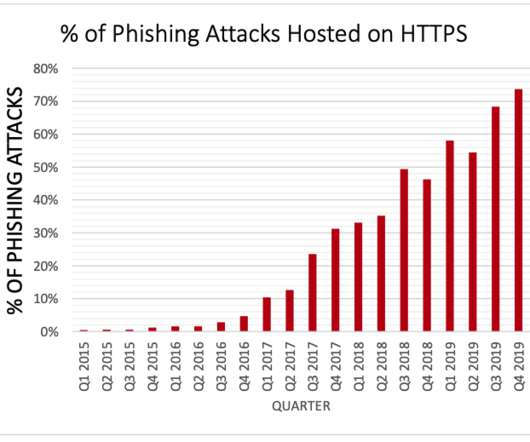
government Web sites now carry a message prominently at the top of their home pages meant to help visitors better distinguish between official U.S. government properties and phishing pages. Census Bureau website [link] carries a message that reads, “An official Web site of the United States government.













































Let's personalize your content