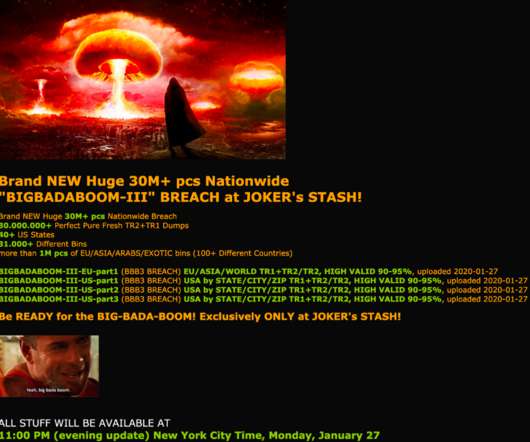
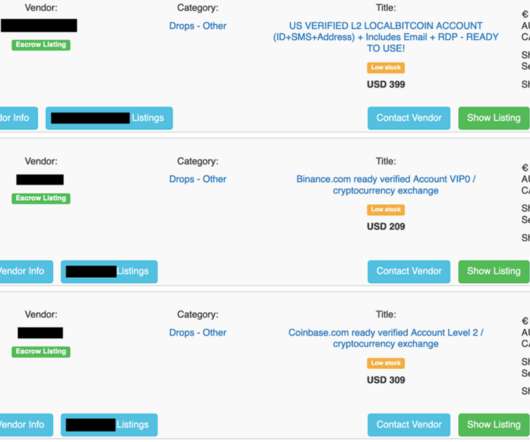
Wawa Breach May Have Compromised More Than 30 Million Payment Cards
Krebs on Security
JANUARY 28, 2020
said a nine-month-long breach of its payment card processing systems may have led to the theft of card data from customers who visited any of its 850 locations nationwide. The exposed information includes debit and credit card numbers, expiration dates, and cardholder names. On the evening of Monday, Jan.























Let's personalize your content