Vice Society gang is using a custom PowerShell tool for data exfiltration
Security Affairs
APRIL 17, 2023
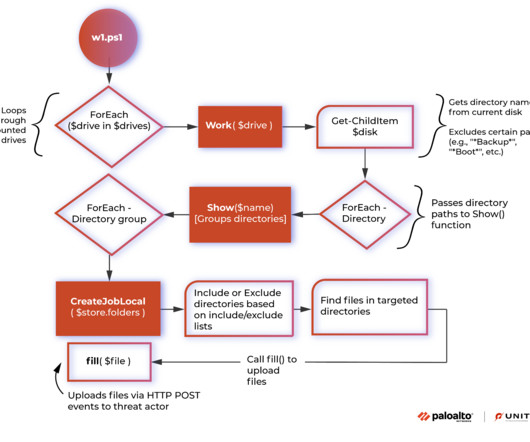
Vice Society ransomware operators have been spotted using a PowerShell tool to exfiltrate data from compromised networks. Threat actors are using the PowerShell tool to evade software and/or human-based security detection mechanisms. The script ignores files that are under 10 KB in size and that do not have a file extension.












































Let's personalize your content