Top Deception Tools for 2022
eSecurity Planet
APRIL 11, 2022
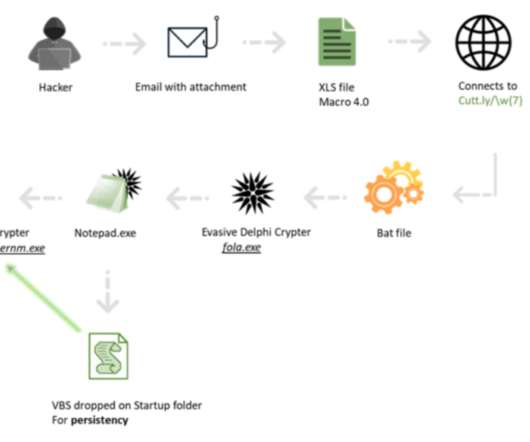
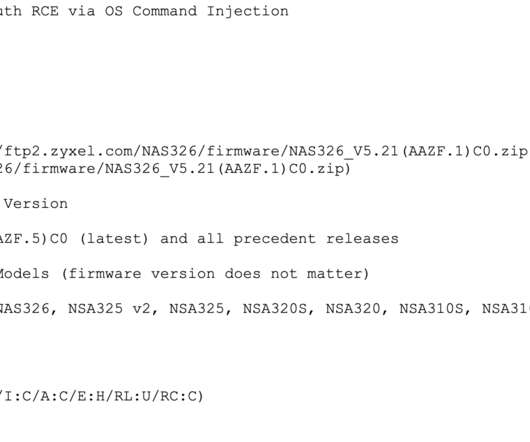
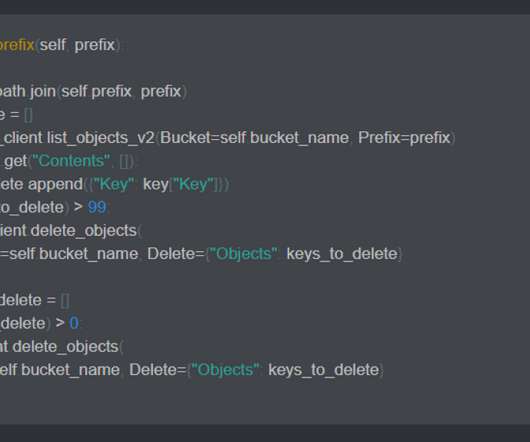
Security vendors and startups use deception techniques to confuse and befuddle attackers. If an attacker is spending time and energy breaking into a decoy server, the defender is not only protecting valuable assets, but also learning about the attacker’s objectives, tools, tactics, and procedures. But it can work the other way.












































Let's personalize your content