NEW TECH: Trend Micro inserts ‘X’ factor into ‘EDR’ – endpoint detection and response
The Last Watchdog
AUGUST 14, 2019
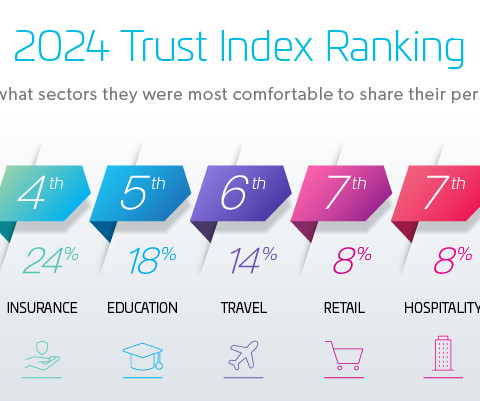
Related: Lessons learned from Capital One breach Yet, I also had the chance to speak one-on-one with dozens of security vendors who are innovating like crazy to improve security. I met with Kevin Simzer, for instance, Trend Micro’s chief operating officer. And I came away, once again, much encouraged.














































Let's personalize your content