Operation Blacksmith: Lazarus exploits Log4j flaws to deploy DLang malware
Security Affairs
DECEMBER 12, 2023
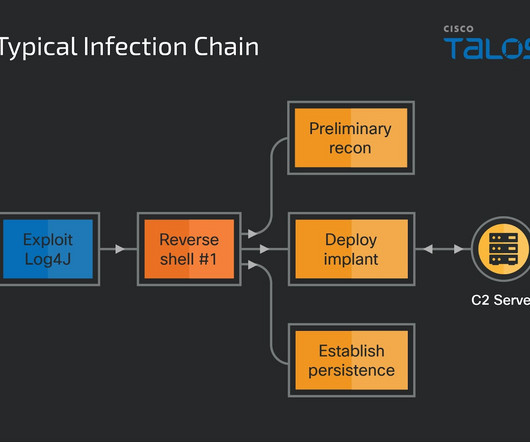
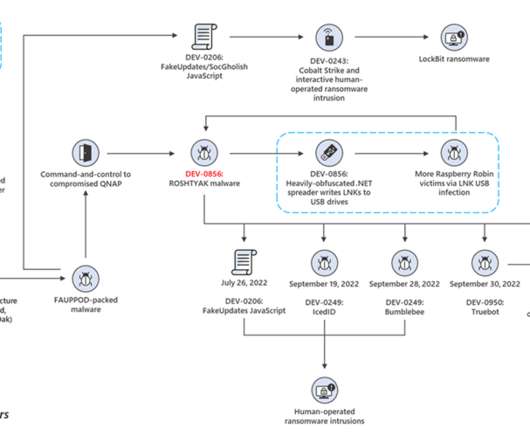
The experts observed the use of NineRAT at around September 2023 against a European manufacturing entity. Lazarus APT is an umbrella for sub-groups, each of them has specific objectives in defense, politics, national security, and research and development. In March, the threat actors hit a South American agricultural organization.












































Let's personalize your content