News Alert: CrowdSec report highlights the rise of IPv6 in cyber criminal activities
The Last Watchdog
JULY 27, 2023
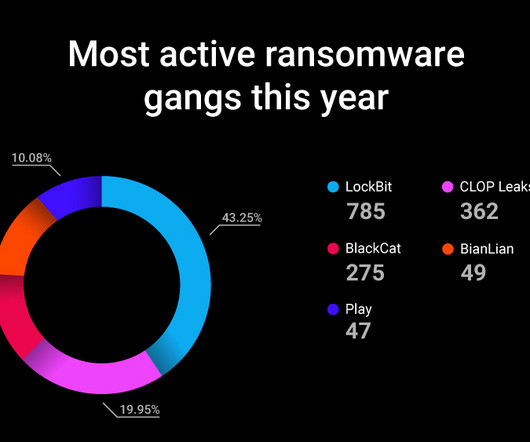
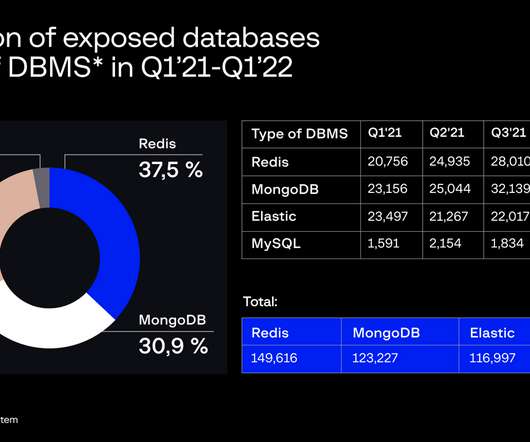
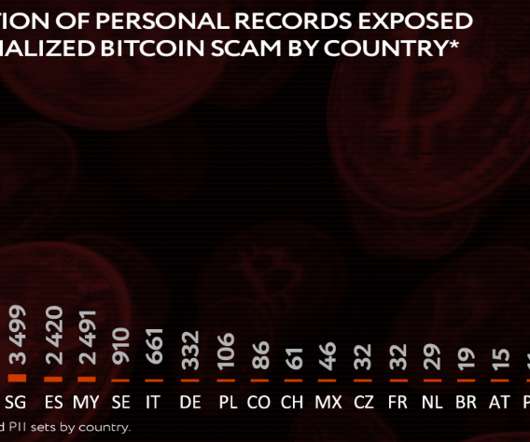
Paris, France, July 27, 2023 – CrowdSec , the pioneering open source and collaborative cybersecurity company, today released its Q2 2023 Majority Report , a comprehensive community-driven data report fueled by the collective efforts of its thousands of users. Malevolent Duration (MD) is a more accurate metric for evaluating AS.


















































Let's personalize your content