Enhance your data security posture with a no-code approach to application-level encryption
IBM Big Data Hub
MAY 23, 2024
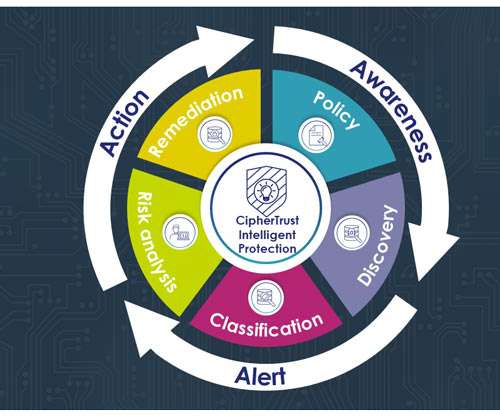
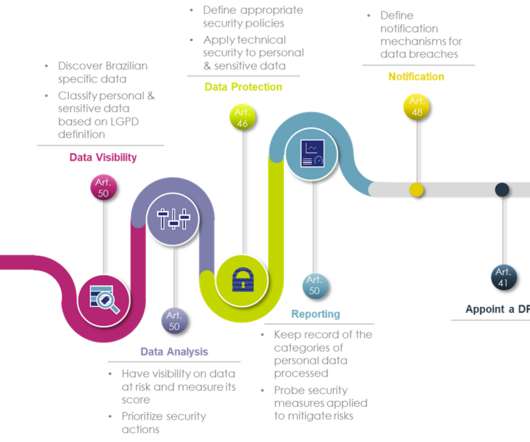
While there are different mechanisms available to encrypt data throughout its lifecycle ( in transit , at rest and in use ), application-level encryption (ALE) provides an additional layer of protection by encrypting data at its source. Why should you consider application-level encryption?


















































Let's personalize your content