Researchers show how to steal a Tesla Model X in a few minutes
Security Affairs
NOVEMBER 23, 2020
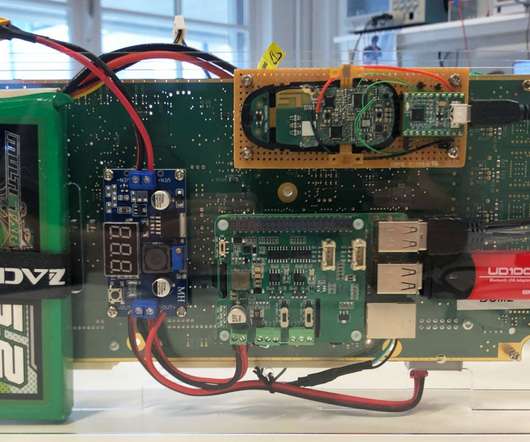
Boffins have demonstrated how to steal a Tesla Model X in a few minutes by exploiting vulnerabilities in the car’s keyless entry system. The key fob used in Tesla Model X communicates with the vehicle with Bluetooth Low Energy (BLE). Pierluigi Paganini. SecurityAffairs – hacking, Tesla Model X).











































Let's personalize your content