Why organizational buy-in is critical to data cloud migration
Collibra
FEBRUARY 21, 2024
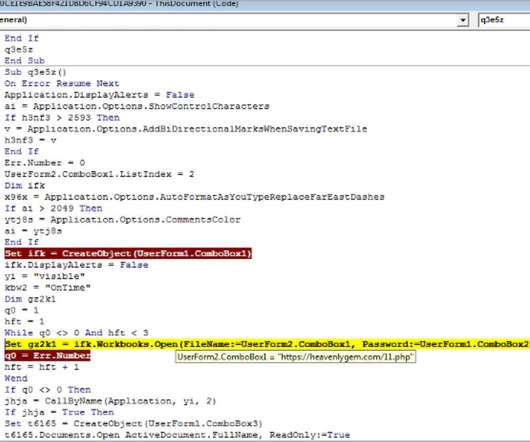
Migrating to the cloud but worried your organization — or your data — isn’t up to the challenge? To achieve data cloud migration success, we recommend a 4-step process that we explore in our helpful ebook: Four steps to successfully power your data cloud migration with data intelligence.















































Let's personalize your content