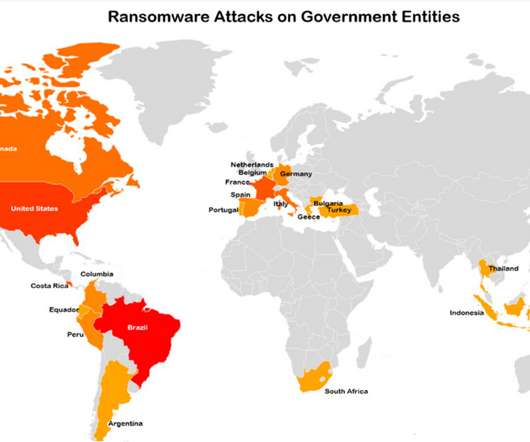
Experts warn of ransomware attacks against government organizations of small states
Security Affairs
MAY 31, 2022
“Typically, cyberattacks on small nations by state-sponsored and renowned APTs are adopted by a few sponsoring nations to impact the socio-politico fabric and gain a political and diplomatic edge when it comes to trade and investment.” ” concludes the report. To nominate, please visit:?. Pierluigi Paganini.











































Let's personalize your content