Zimbra zero-day exploited to steal government emails by four groups
Security Affairs
NOVEMBER 16, 2023
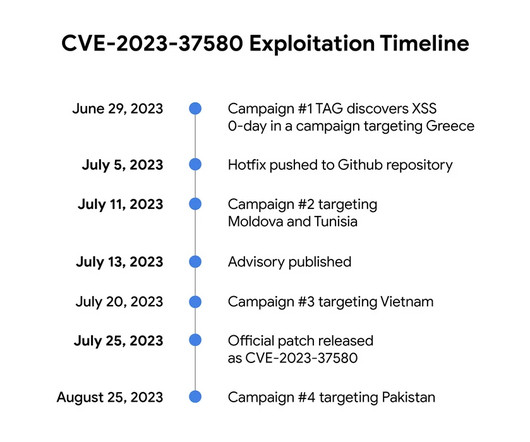
Google TAG revealed that threat actors exploited a Zimbra Collaboration Suite zero-day ( CVE-2023-37580 ) to steal emails from governments. Google TAG researcher Clément Lecigne discovered the zero-day in June while investigating targeted attacks against Zimbra’s email server. ” reads the advisory published by Google TAG.























Let's personalize your content