Earth Krahang APT breached tens of government organizations worldwide
Security Affairs
MARCH 19, 2024
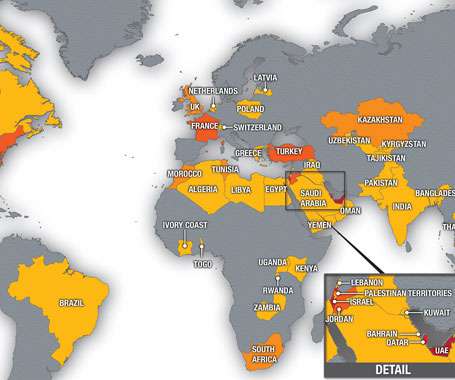
The campaign seems active since at least early 2022 and focuses primarily on government organizations. The group often exploited access to government infrastructure to target other government entities. In many attacks, the group scanned public-facing servers with open-source scanning tools.








































Let's personalize your content