Security Analysis of Threema
Schneier on Security
JANUARY 19, 2023
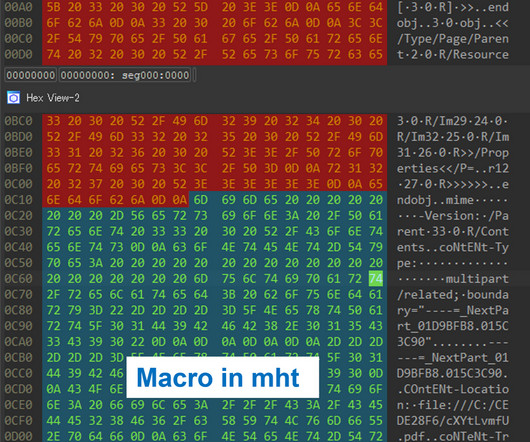
A group of Swiss researchers have published an impressive security analysis of Threema. We provide an extensive cryptographic analysis of Threema, a Swiss-based encrypted messaging application with more than 10 million users and 7000 corporate customers.












































Let's personalize your content