National Safety Council data leak: Credentials of NASA, Tesla, DoJ, Verizon, and 2K others leaked by workplace safety organization
Security Affairs
AUGUST 31, 2023
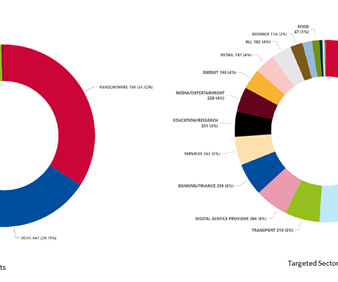
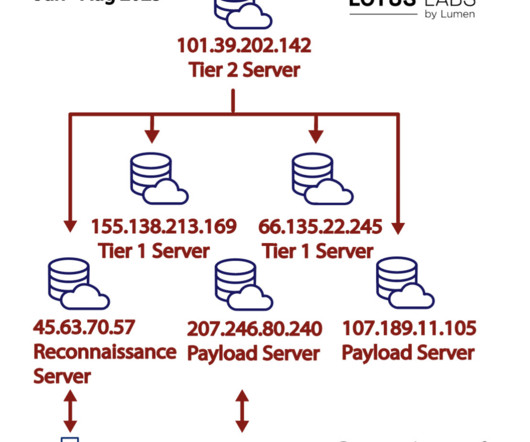
The Cybernews research team discovered public access to the web directories that exposed thousands of credentials. Also, the credentials could have been used to gain initial access into corporate networks to deploy ransomware, steal or sabotage internal documents, or gain access to user data.












































Let's personalize your content