Improve manufacturing access to released product information
OpenText Information Management
FEBRUARY 16, 2023
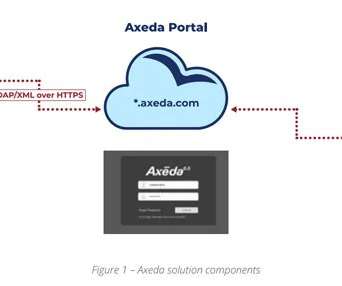
The manufacturing of products relies on numerous activities supported by disconnected processes and applications that produce a steady flow of product-related content. But most of this information is housed in siloed applications, making content difficult for stakeholders to access.












































Let's personalize your content