Root Admin User: When Do Common Usernames Pose a Threat?
Data Breach Today
SEPTEMBER 11, 2023
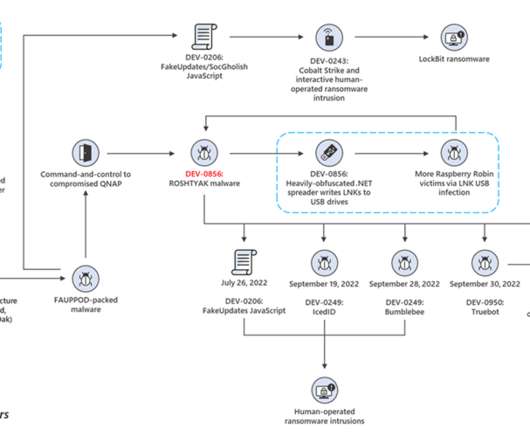
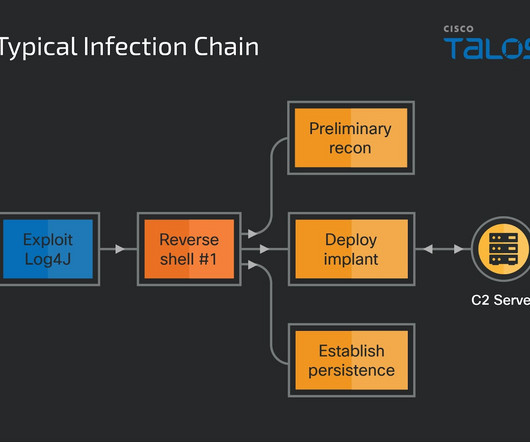
Honeypot Hits Reinforce Need for Strong Passwords and Multifactor Authentication Honeypot data collected by CISO Jesse La Grew highlights how attackers continue to target default usernames - including for SSH - together with weak passwords to gain brute force remote access to their targets.












































Let's personalize your content