Monitoring the dark web to identify threats to energy sector organizations
Security Affairs
MAY 17, 2023
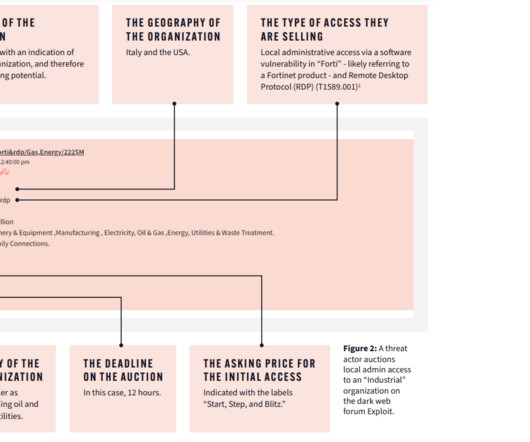
Searchlight Cyber researchers warn of threat actors that are offering on the dark web access to energy sector organizations. Dark web intelligence firm Searchlight Cyber published a report that analyzes how threat actors in the dark web prepare their malicious operations against energy organizations.













Let's personalize your content