Microsoft 365 Research Highlights Cloud Vulnerabilities
eSecurity Planet
JUNE 21, 2022
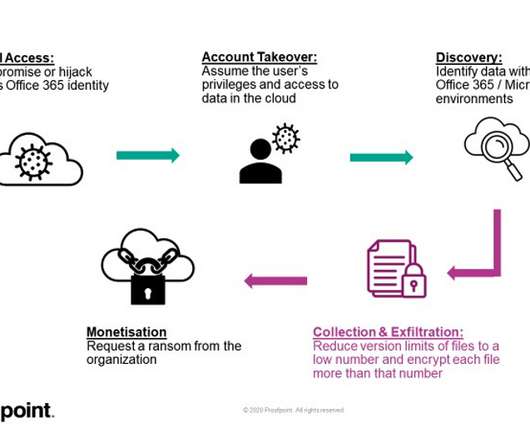
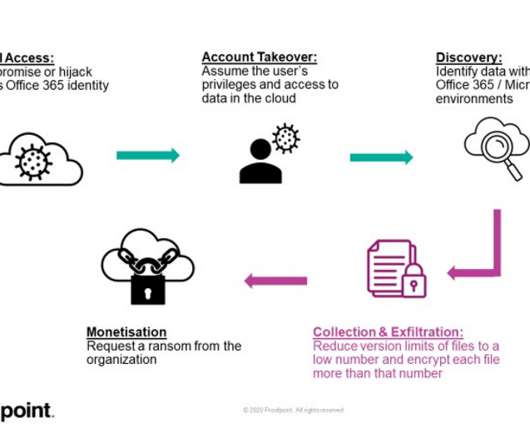
In a sequence that suggests cloud services may be more vulnerable than many think, Proofpoint researchers have demonstrated how hackers could take over Microsoft 365 accounts to ransom files stored on SharePoint and OneDrive. Hackers could also trick users into authorizing rogue third-party apps to access the scope for SharePoint or OneDrive.







































Let's personalize your content