Calculating electronic records storage costs
The Schedule
APRIL 14, 2020
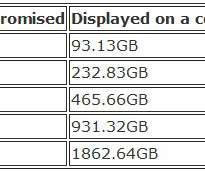
This post will do the same for electronic records and follows the same formula of not taking into account personnel or overhead costs or depreciation of equipment. If you prefer a truncated version of this information, I’ve created a 1-page brochure of questions to consider about electronic records storage costs. On-Premise Storage.











































Let's personalize your content