Experts Explain How to Bypass Recent Improvement of China’s Great Firewall
Security Affairs
JANUARY 31, 2021
Last year, the group published a detailed analysis on how the Chinese government has improved its surveillance system to detect and block the popular circumvention tools Shadowsocks and its variants. ” reads the paper published by the experts. ” reads the paper published by the experts. Pierluigi Paganini.


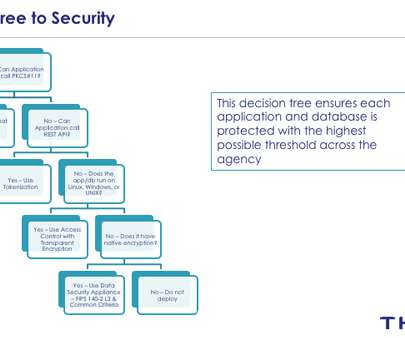

















Let's personalize your content