MY TAKE: Is Satya Nadella’s ‘Secure Future Initiative’ a deja vu of ‘Trustworthy Computing?’
The Last Watchdog
MAY 3, 2024
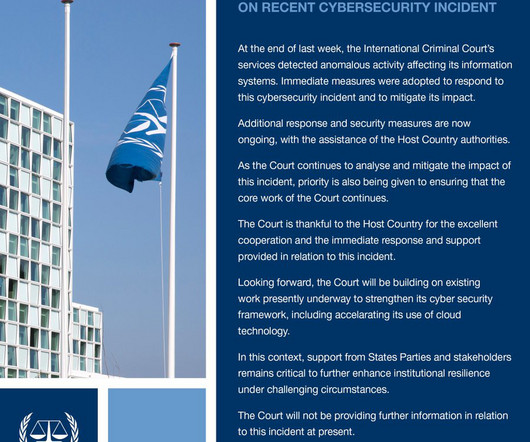
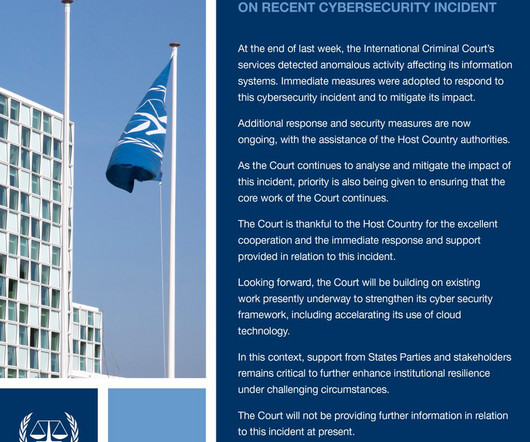
Screenshot In a huge development, Microsoft announced today that it is revising its security practices, organizational structure, and, most importantly, its executive compensation in an attempt to shore up major security issues with its flagship product, not to mention quell rising pressure from regulators and customers.








































Let's personalize your content