Enhancing triparty repo transactions with IBM MQ for efficiency, security and scalability
IBM Big Data Hub
MAY 24, 2024
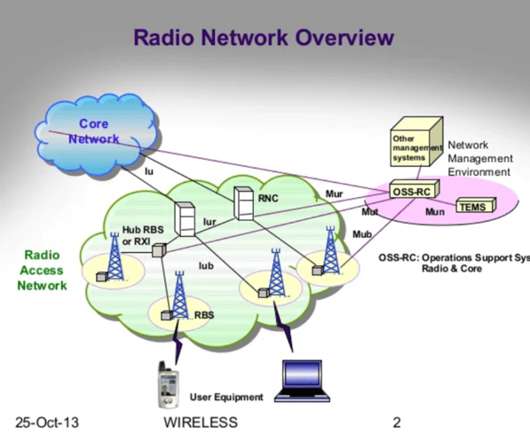
The exchange of securities between parties is a critical aspect of the financial industry that demands high levels of security and efficiency. Triparty repo dealing systems, central to these exchanges, require seamless and secure communication across different platforms.































Let's personalize your content