Remembering 9/11 Attacks – A Moment of Silence
IG Guru
SEPTEMBER 11, 2020
On 9/11/2001 the attacks on the World Trade Centers began. Let us never forget. The post Remembering 9/11 Attacks – A Moment of Silence appeared first on IG GURU.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
 2001 Related Topics
2001 Related Topics 
IG Guru
SEPTEMBER 11, 2020
On 9/11/2001 the attacks on the World Trade Centers began. Let us never forget. The post Remembering 9/11 Attacks – A Moment of Silence appeared first on IG GURU.

Data Matters
OCTOBER 20, 2022
Treasury Department is seeking public comment on the need and scope for a potential federal insurance response to catastrophic cyber incidents, akin to the one put in place for terrorism insurance after the attacks of September 11, 2001. The post U.S.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 28, 2024
formerly known as AmerisourceBergen, is an American drug wholesale company and a contract research organization that was formed by the merger of Bergen Brunswig and AmeriSource in 2001. Cencora, Inc. The Company had $238.6 billion in revenue for fiscal year 2022 and had approximately 44,000 employees.

The Last Watchdog
JUNE 27, 2023
Swissbit was founded in 2001 and has offices in Switzerland, Germany, USA, Japan and Taiwan. Swissbit’s storage range includes SSDs with PCIe and SATA interface such as mSATA, Slim SATA, CFast™, M.2 2 and 2.5” as well as CompactFlash, USB flash drives, SD Memory Cards, microSD Memory Cards and managed NAND BGAs like e.MMC.

Speaker: Elizabeth "Paige" Baumann, Founder and CEO of Paige Baumann Advisory, LLC
anti-money laundering laws since the USA PATRIOT Act of 2001. In this webinar, you'll be provided with a clear overview of the Anti-Money Laundering Act of 2020 (AMLA), which also includes the Corporate Transparency Act (CTA). The AMLA represents the most significant changes in U.S.

AIIM
APRIL 7, 2020
As a paid professional member of both since 2001 – August 2001 for AIIM, September 2001 for ARMA, and having served on both organizations’ Board of Directors (2004-2005 for AIIM, 2007-2010 for ARMA), I have thoughts on both and will compare them in several key areas, including: Focus.

IG Guru
FEBRUARY 26, 2021
14, 2001), the 5th Circuit struck down a fine and enforcement action by HHS as arbitrary and capricious. Court of Appeals for the 5th Circuit just issued a blistering attack on HIPAA enforcement by the U.S. Department of Health and Human Services (HHS). In University of Texas M.D. Anderson Cancer v. 19-60226, Jan. The post The M.D.
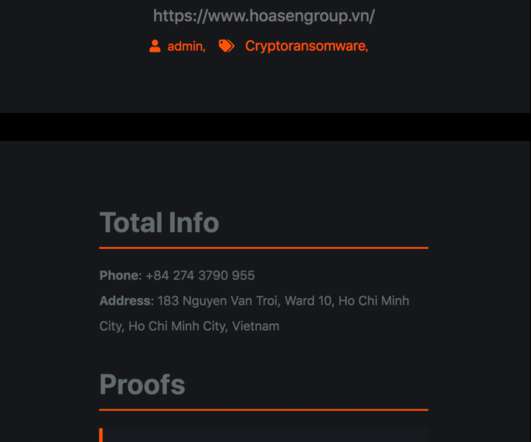
Security Affairs
AUGUST 21, 2020
The Hoa Sen Group (HSG) was founded in the year 2001, it has 7,100 employees across all its 343 companies and has been earning annual revenue of around $1.18 Hoa Sen Group is the no.1 1 company in the field of manufacturing and trading steel sheet in Vietnam and the leading exporter of steel sheet in Southeast Asia.

IG Guru
SEPTEMBER 11, 2019
June 19 2019 via BBC News Archivists who bought a stash of CDs at a house clearance sale found 2,400 photos of Ground Zero in New York taken following the 9/11 attacks in 2001. They appear to have been taken by an as yet unidentified construction worker who helped to clear up the wreckage of […].

AIIM
FEBRUARY 18, 2021
Now that we've taken a look at a common business scenario without a Records Management program, let's really dig into the value of what Records Management can bring to the table. Learn more in AIIM's Glossary Page ).
Krebs on Security
FEBRUARY 7, 2024
Launched in 2001 under the tagline “Network terrorism,” Mazafaka would evolve into one of the most guarded Russian-language cybercrime communities.

John Battelle's Searchblog
JULY 9, 2024
It took two decades for that promise to be met, but in a span of less than five years – 1997-2001 – Webvan raised nearly a billion dollars, went public, and filed for bankruptcy. Remember Webvan , the celebrated startup that was going to deliver groceries to homes across the country?

OpenText Information Management
JUNE 20, 2019
Nick is the firm’s lead analyst for AI and machine learning, an area he has been researching since 2001. Note: This blog is by guest author Nick Patience, Founder & Research Vice President of 451 Research. Almost every company wants to be data-driven.

Hunton Privacy
SEPTEMBER 14, 2021
The Centre for Information Policy Leadership (“CIPL”), a global privacy and security think tank founded in 2001 by leading companies and Hunton Andrews Kurth LLP, is celebrating 20 years of working with industry leaders, regulatory authorities and policymakers to develop global solutions and best practices for privacy and responsible data use.

IBM Big Data Hub
MAY 24, 2024
CCIL) is a central counterparty (CCP) that was set up in April 2001 to provide clearing and settlement for transactions in government securities, foreign exchange and money markets in the country. This will help reduce errors and miscommunications, enabling transactions to be executed correctly.

Security Affairs
JULY 25, 2022
“The Revenue Agency, operational since 1 January 2001, was born from the reorganization of the Financial Administration following the Legislative Decree No. 300 of 1999. It has its own statute and specific regulations governing administration and accounting.
Archive-It
SEPTEMBER 8, 2021
It will more easily facilitate future feature developments and continues the legacy of Wayback software as the original, most widely used, and most actively maintained web archive replay tool since its original release in 2001. Wayback Machine access on archive.org in 2001.

Info Source
JANUARY 11, 2018
After holding senior positions with Siemens AG and construction software specialist Nemetschek, Max Ertl joined DocuWare in 2001 with responsibility for marketing. million in 2001 to around € 44 million in 2017. During his tenure, global sales have risen from € 6.3 He was promoted to Chief Revenue Officer on January 1, 2018.

IG Guru
JANUARY 25, 2019
Track 1: Becoming a Certified Information Governance Professional (IGP) Track 2: ICRM Exam Prep: Introduction and Parts 1-6 (CRM): Event – Apache Corporation Conference Center 2000 Post Oak Boulevard, Houston, Texas 77056-4400 Hotel – Hilton Houston Post Oak by the Galleria 2001 Post Oak […].

John Battelle's Searchblog
JUNE 19, 2023
Then, of course, the hype overwhelmed the technology’s ability to deliver, and it all came crashing down in 2001. All of those things and more had to be invented from scratch, and it took several years before the entrepreneurial ecosystem ramped up to the challenge.

Krebs on Security
FEBRUARY 8, 2019
The USA Patriot Act , passed in the wake of the terror attacks of Sept 11, 2001, requires all financial institutions to appoint at least two Bank Secrecy Act (BSA) contacts responsible for reporting suspicious financial transactions that may be associated with money laundering.
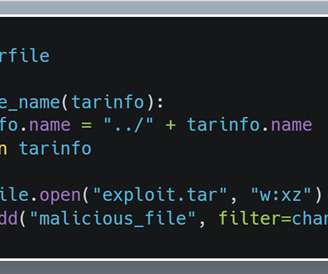
Security Affairs
SEPTEMBER 22, 2022
dot dot) sequence in filenames in a TAR archive, a related issue to CVE-2001-1267. The issue is a Directory traversal vulnerability that resides in the ‘extract’ and ‘extractall’ functions in the tarfile module in Python. A user-assisted remote attacker can trigger the issue to overwrite arbitrary files via a.

Hunton Privacy
DECEMBER 19, 2022
It was a truly spectacular event, the first of its kind, bringing together the good and the great in the world of privacy and shining a light on incredible talent,” added Partner Sarah Pearce , “I am thrilled for Rosemary.

Data Matters
OCTOBER 20, 2022
Treasury Department is seeking public comment on the need and scope for a potential federal insurance response to catastrophic cyber incidents, akin to the one put in place for terrorism insurance after the attacks of September 11, 2001.

Krebs on Security
MARCH 26, 2020
” According to cyber intelligence firm Intel 471 , Stroganov has been a long-standing member of major underground forums since at least 2001. The post claimed that among those apprehended was the infamous cybercriminal Alexey Stroganov, who goes by the hacker names “Flint” and “Flint24.”

Krebs on Security
FEBRUARY 12, 2019
Founded in 2001 and based in Milwaukee, Wisc., Email provider VFEmail has suffered what the company is calling “catastrophic destruction” at the hands of an as-yet unknown intruder who trashed all of the company’s primary and backup data in the United States. VFEmail provides email service to businesses and end users.

eDiscovery Daily
APRIL 1, 2019
As always, the best resource for tracking eDiscovery Mergers, Acquisitions, and Investments is Rob Robinson’s ComplexDiscovery site – after all, Rob via ComplexDiscovery has noted more than 375 M&A+I events between November 2001 and today. To wit: Q1 2019’s 16 transactions are more than all but one year from 2001 to 2009.

The Last Watchdog
DECEMBER 10, 2018
About the essayist: Todd Feinman is president and CEO of Identity Finder , co-founding the company in 2001. May these recent disheartening examples in the news spur brands to act today and take action to protect sensitive data and avoid the far-reaching negative impacts of high-profile data breaches.

Archives Blogs
DECEMBER 21, 2018
It was produced by WNYC’s Scott Borden and Gads Hill for a broadcast on February 11, 2001. The story of Lancelot and Elaine is based on Alfred Lord Tennyson’s poem Idylls of the King. The production features Christopher Cartmill and Kathleen O’Grady. Jo Ann Allen introduces the production.

Archives Blogs
SEPTEMBER 16, 2020
On September 18, 2001, The late Richard Hake sat-in for Brian Lehrer at Columbia University’s new studios at WKCR. Just one week after the attack on the World Trade Center, WNYC was broadcasting on FM at reduced power from the Empire State Building and over WNYE (91.5

AIIM
NOVEMBER 17, 2017
Since its humble beginnings in 2001, it has grown to nearly 200 million seats and is found in every industry sector. It's hard to overestimate the impact of SharePoint on the information management market. If you're reading this blog post, you likely have SharePoint in your organization.

Schneier on Security
NOVEMBER 19, 2018
Let's ask the question more generally: why hasn't there been another 9/11 since 2001? These are all good reasons, but I think both authors missed the most important one: there simply aren't a lot of terrorists out there. But since then, nothing.

Archives Blogs
APRIL 23, 2020
In the mid-1990s, Co-op Radio moved locations to 337 Carrall Street and then again to 370 Columbia in 2001. Cover of Co-operative Radio Listener’s Guide (April/June 2001). The station aired its first show on April 14, 1975 and has been on the air ever since. ” Panelists include: Pratibha Parmar, Loretta Todd and Ayoka Chenzira.

Armstrong Archives
MARCH 13, 2024
In 2001, just 18% of U.S.-based based physicians were using electronic medical record (EMR) or electronic health record (EHR) systems. As of 2021, that figure has soared to 88%. Healthcare organizations across the nation have embraced EHRs, largely thanks to their ability to reduce staff burnout and increase efficiency.

Schneier on Security
APRIL 20, 2020
Since 2001 Microsoft has collected 13 million work items and bugs. To better label and prioritize bugs at that scale, we couldn't just apply more people to the problem. However, large volumes of semi-curated data are perfect for machine learning.

The Last Watchdog
MARCH 21, 2019
The San Jose, CA-based security vendor has been helping companies protect their web applications since the company was founded in 2001 by world-renowned ethical hacker Jeremiah Grossman , who also happens to be a black belt in Brazilian Jiu-Jitsu, as well as a native of my home state, Hawaii.

Security Affairs
SEPTEMBER 30, 2018
The Estonian electronic ID cards have been manufactured by the Swiss company Trub AG and its successor Gemalto AG since 2001. At the time, Estonia had issued 1.3 million electronic ID cards offering citizens online access to a huge number of services through the “e-government” state portal.

Data Matters
MAY 3, 2021
According to the Proposal, a vaccine certificate should be issued by Member States for COVID-19 vaccines (a) that have received marketing authorisation pursuant to Regulation 726/2004, or pursuant to Directive 2001/83/EC, or (b) the distribution of which has been temporarily authorised pursuant to Article 5(2) of Directive 2001/83/EC.

Unwritten Record
OCTOBER 6, 2020
Another area we should recognize is the rise of Hispanic Heritage artistic themes and communities in the US.

DLA Piper Privacy Matters
APRIL 20, 2021
The Draft SCCs would repeal the existing SCCs (dating from 2001, 2004 and 2010) and would introduce one set of modular SCCs, useable in the four different scenarios or “modules” (either controller to controller, controller to processor, processor to processor, or processor to controller).

The Last Watchdog
AUGUST 2, 2018
The National Cyber Security Alliance is a non-profit group, underwritten by the top tech companies and biggest banks, that has been out there since 2001 promoting best practices and supplying programs to engrain this mindset in our society. Related: Using ‘gamification’ for security training.

eDiscovery Daily
MARCH 31, 2020
As always, Rob provides a list of M&A+I events between November 2001 and current ( 419 of them), so feel free to check those out — they are always interesting. So, what do you think? How have the challenges of various sources of data affected your organization?

Info Source
OCTOBER 19, 2018
Max Ertl joined DocuWare in 2001. million in 2001 to approximately € 44 million in 2017. He was promoted to Chief Technology Officer at the beginning of 2016. Dr. Michael Berger will assume global responsibility of products, services and finance. Max Ertl will assume global responsibility for sales and marketing.

Archives Blogs
JULY 6, 2020
Portrait of Professor Andrew Miller CBE FRSE, Prinicipal and Vice Chancellor 1994-2001 by Juliet Wood (oil on canvas, 2001). Portrait of Professor Colin Bell, Principal and Vice Chancellor (2001-2003) © Tricia Malley Ross Gillespie www.broaddaylightltd.co.uk.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content