Mitigating Risk With Threat Intelligence
Dark Reading
JULY 5, 2023
Dark Reading's latest publication looks at a missing, but necessary, ingredient to effective third-party risk management.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 threat-intelligence mitigating-risk-with-threat-intelligence
threat-intelligence mitigating-risk-with-threat-intelligence 
Dark Reading
JULY 5, 2023
Dark Reading's latest publication looks at a missing, but necessary, ingredient to effective third-party risk management.

The Last Watchdog
SEPTEMBER 11, 2023
Related: Neutralizing insider threats This pervasive problem extends beyond traditional notions of fraud, encompassing both insider threats and external risks arising from partnerships, competitors, and poor IP management. Organizations must prioritize data and decision intelligence to tackle these threats effectively.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
AUGUST 29, 2023
The threat of bad actors hacking into airplane systems mid-flight has become a major concern for airlines and operators worldwide. Here’s what you should know about the risks, what aviation is doing to address those risks, and how to overcome them. It is difficult to deny that cyberthreats are a risk to planes.

Thales Cloud Protection & Licensing
MARCH 24, 2024
Data Security Trends: 2024 Report Analysis madhav Mon, 03/25/2024 - 05:08 Amid ongoing economic uncertainty and a progressively complex threat landscape, businesses are trying to navigate increasingly stringent regulatory requirements while bolstering their security posture. Alarmingly, 16% admitted to hardly classifying any of their data.

The Last Watchdog
JUNE 2, 2022
Third-Party Risk Management ( TPRM ) has been around since the mid-1990s – and has become something of an auditing nightmare. Related: A call to share risk assessments. This is because third-party risk has become a huge problem for enterprises in the digital age. Cyber risks profiling. based CyberGRX.

The Last Watchdog
NOVEMBER 15, 2021
Such a transformation however, comes with its own set of risks. Misleading information has emerged as one of the leading cyber risks in our society, affecting political leaders, nations, and people’s lives, with the COVID-19 pandemic having only made it worse. So, how do organizations prepare against such threats?

The Last Watchdog
FEBRUARY 20, 2024
Health care relies on it for intelligent symptom analysis and health information dissemination. Inadequate authorization controls may result in unapproved interactions and data exposure, posing significant security threats. Machine learning helps AI chatbots adapt to and prevent new cyber threats. These tools saved 2.5

The Last Watchdog
AUGUST 17, 2022
Security teams must defend an expanding attack surface, skilled IT professionals are scarce and threat actors are having a field day. They’ve progressed to supplying EDR, SIEM, threat intelligence and other advanced services on an outsourced basis. Network security is in dire straits. Can the MSSPs pull off the heroics?

IBM Big Data Hub
MARCH 25, 2024
For other financial services firms outside of the insurance sector, property accepted as loan security might face climate-related risks as well. Longer-term local climate change risks might still devalue property that hasn’t suffered damage. These climate events have a huge potential impact on financial institutions.

The Last Watchdog
JULY 11, 2023
Boston, July 7, 2023 — CybSafe, the human risk management platform, has today announced CEO Oz Alashe MBE has been named as a SecurityInfoWatch.com , Security Business and Security Technology Executive magazines’ 2023 Security Industry Innovator Award winner. We are developing intelligent software to help them.”

Security Affairs
DECEMBER 5, 2023
Microsoft’s Threat Intelligence is warning of Russia-linked cyber-espionage group APT28 (aka “Forest Blizzard”, “Fancybear” or “Strontium”) actively exploiting the CVE-2023-23397 Outlook flaw to hijack Microsoft Exchange accounts and steal sensitive information.

eSecurity Planet
AUGUST 10, 2023
Threat intelligence feeds are continually updated streams of data that inform users of different cybersecurity threats, their sources, and any infrastructure impacted or at risk of being impacted by those threats.

Dark Reading
FEBRUARY 23, 2018
In order to get the maximum benefit from threat intel you need to be able to operationalize it. Here's how.

Security Affairs
FEBRUARY 14, 2024
Multiple nation-state actors are exploiting artificial intelligence (AI) and large language models (LLMs), including OpenAI ChatGPT, to automate their attacks and increase their sophistication. ” reads the report published by Microsoft. ” reads the report published by Microsoft.

OpenText Information Management
MAY 1, 2024
Before we delve into these findings, we want to celebrate a milestone: 2024 marks the 10th consecutive year that the OpenText ArcSight Intelligence™ team has contributed to the DBIR. From falling victim to phishing attacks to insider threats, employees continue to be vulnerable to exploitation by threat actors.
eSecurity Planet
JUNE 18, 2021
There’s a never ending cycle between the measures cybersecurity providers introduce to prevent or remediate cyber threats and the tactics cyber criminals use to get around these security measures. As soon as a security company develops a way to mitigate the latest threat, attackers develop a new threat to take its place.

eSecurity Planet
DECEMBER 20, 2023
Attack surface management aims to automate the process of discovering, assessing, and prioritizing vulnerabilities and third-party, digital supply chain, and cloud risks. It addresses both internal and external (EASM) risks. CAASM (cyber asset ASM) and DRPS (digital risk protection) are also related terms and elements of ASM.

OpenText Information Management
MAY 6, 2024
Many organizations are in the exploratory phases of using Artificial Intelligence (AI). As per Forbes , the global artificial intelligence market is projected to reach $1.8k Some of these AIs include machine learning (ML), and natural language processing (NLP) in the AI category, which makes AI more inclusive. billion by 2030.

The Last Watchdog
AUGUST 13, 2023
Artificial intelligence has been in commercial use for many decades; Markstedter recounted why this potent iteration of AI is causing so much fuss, just now. Threat intelligence vendor Cybersixgill for instance launched Cybersixgill IQ at Black Hat. Island supplies an advanced web browser security solution.

IBM Big Data Hub
SEPTEMBER 6, 2023
Every one of these assets plays a vital role in business operations—and any of them could contain vulnerabilities that threat actors can use to sow chaos. a bug in a web app that lets threat actors inject the system with malware —are a common type of vulnerability. Coding errors—e.g.,

The Last Watchdog
JULY 26, 2023
July 26, 2023 — Protect AI , the artificial intelligence (AI) and machine learning (ML) security company, today announced it has closed a $35M Series A round of funding. to help organizations protect ML systems and AI applications from unique security vulnerabilities, data breaches and emerging threats. Seattle, Wash.,

eSecurity Planet
FEBRUARY 17, 2023
Threat hunting starts with a pretty paranoid premise: That your network may have already been breached and threat actors may be inside waiting for an opportunity to strike. Threat hunting teams are often composed of analysts from SOC teams or similarly qualified security pros. Sadly, that turns out to be true in many cases.

Hunton Privacy
OCTOBER 30, 2023
On October 30, 2023, the G7 leaders announced they had reached agreement on a set of International Guiding Principles on Artificial Intelligence (AI) and a voluntary Code of Conduct for AI developers, pursuant to the Hiroshima AI Process.

The Last Watchdog
SEPTEMBER 7, 2022
Meanwhile, Level 3, calls for several more tiers of protection specifically aimed at reducing the risk from Advanced Persistent Threats ( APTs ) in order to safeguard so-called Controlled Unclassified Information ( CUI.). Cybersecurity Maturity Model Certification version 2.0 It’s a milestone, for sure,” Jimenez told me.

eSecurity Planet
JULY 16, 2021
Incident response tools can help implement incident response plans and elevate response plans from a manual to an automated basis, sandboxing threats and shutting down ports and access and the like. And more than ever, they also need an incident response service that can step in to help clean up those messes. Key Differentiators.

IBM Big Data Hub
MAY 8, 2024
The risk of valid identities being used as the entry point by bad actors is expected to continue with the ever-increasing applications and systems being added in today’s hybrid environments. As a result, the interpretation of the varied risk signals is siloed across different events along the digital user journey.

IBM Big Data Hub
APRIL 15, 2024
The latest findings of the IBM X-Force® Threat Intelligence Index report highlight a shift in the tactics of attackers. Challenges of traditional security awareness programs Most security awareness programs today provide employees with information they need about handling data, GDPR rules and common threats, such as phishing.
eSecurity Planet
DECEMBER 29, 2021
It’s based on practical use cases, so companies can better evaluate security issues and get examples of common tactics and techniques used by threat actors. According to MITRE, there are four primary use cases where the document base can be beneficial: Threat intelligence. It provides advanced ability to defeat common attacks.

eSecurity Planet
AUGUST 4, 2023
Cloud Infrastructure Entitlement Management (CIEM): Best used to effectively manage cloud resource entitlements, reduce access risks, and maintain compliance. CWPP provides strong defenses against a wide range of risks such as malware , ransomware , DDoS attacks , configuration errors , insider threats, and data breaches.

eSecurity Planet
JUNE 15, 2023
Vulnerability management is the process of identifying, classifying, remediating, and mitigating vulnerabilities. This includes establishing explicit goals for your organization, such as improving security posture or reducing risk. Examples of external sources you can leverage include threat feeds such as STIX , OpenloC , and MAEC.

IBM Big Data Hub
MARCH 27, 2024
As businesses make plans to mitigate climate risks such as extreme weather events, they have an opportunity to innovate with new business models and demonstrate leadership by implementing more sustainable practices. What is climate risk? To best prepare, organizations need to develop a climate risk strategy.

eSecurity Planet
SEPTEMBER 24, 2021
Rapid7 combines threat intelligence , security research, data collection, and analytics in its comprehensive Insight platform, but how does its detection and response solution – InsightIDR – compare to other cybersecurity solutions? Ease of Implementation, Quick Start Services. Bundling with the Rapid7 Insight Platform.

The Last Watchdog
OCTOBER 24, 2023
Security and risk management leaders must rethink their balance of investments across technology, structural, and human-centric elements as they design and implement their cybersecurity programs.” 2 Each day brings new threats and challenges, further compounded by artificial intelligence (AI).
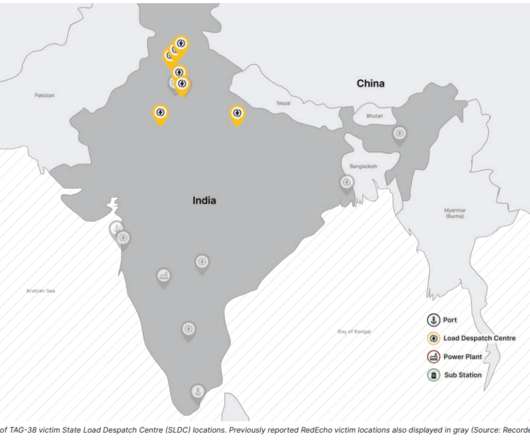
Security Affairs
OCTOBER 15, 2022
Threat actors hit the Information Technology (IT) infrastructure of the company. The Economic Times, citing a senior official from the Maharashtra Police’s cyber unit, confirmed that local authorities warned of a threat to electricity companies in the country, including Tata Power. ” reported The Economic Times.
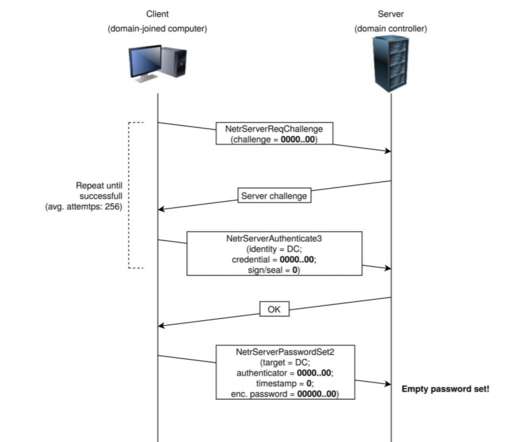
Security Affairs
SEPTEMBER 24, 2020
Microsoft is warning of threat actors that are actively using the Windows Server Zerologon exploits in attacks in the wild. Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon. — Microsoft Security Intelligence (@MsftSecIntel) September 24, 2020.

IBM Big Data Hub
APRIL 24, 2024
While researchers have not yet found a way to completely prevent prompt injections, there are ways of mitigating the risk. However, organizations can significantly mitigate the risk of prompt injection attacks by validating inputs, closely monitoring LLM activity, keeping human users in the loop, and more. The remoteli.io

Security Affairs
JULY 7, 2022
I’m proud to announce that the European Union Agency for Cybersecurity, ENISA, has released the Threat Landscape Methodology. Policy makers, risk managers and information security practitioners need up-to-date and accurate information on the current threat landscape, supported by threat intelligence.

IBM Big Data Hub
FEBRUARY 16, 2024
Like a red team exercise, breach and attack simulations use the real-world attack tactics, techniques, and procedures (TTPs) employed by hackers to proactively identify and mitigate security vulnerabilities before they can be exploited by actual threat actors. How does breach and attack simulation work?

eSecurity Planet
FEBRUARY 21, 2023
The ultimate goal is to understand the advanced threats an organization may face in order to better protect against those adversaries. Learn more about Cybersecurity Risk Management Red Teams Red teams simulate the tactics, techniques, and procedures ( TTPs ) an adversary might use against the organization.

IBM Big Data Hub
DECEMBER 8, 2023
.” This same sentiment can be true when it comes to a successful risk mitigation plan. The only way for effective risk reduction is for an organization to use a step-by-step risk mitigation strategy to sort and manage risk, ensuring the organization has a business continuity plan in place for unexpected events.

Data Matters
JANUARY 28, 2022
The advisory was promptly endorsed by the National Cyber Security Centre, a division of Government Communications Headquarters (“GCHQ”), a UK intelligence agency. First , all of the reports specifically focus on the threat of Russian state-sponsored cyberattacks. Key Takeaways. This is an important public action by the U.S.

IT Governance
MAY 11, 2023
The Eurovision Song Contest is set to take place in Liverpool this weekend, but amid the pageantry and political jostling, organisers are concerned about the threat of a cyber attack. Experts from the NCSC (National Cyber Security Centre) have been brought in to help identify and respond to threats.
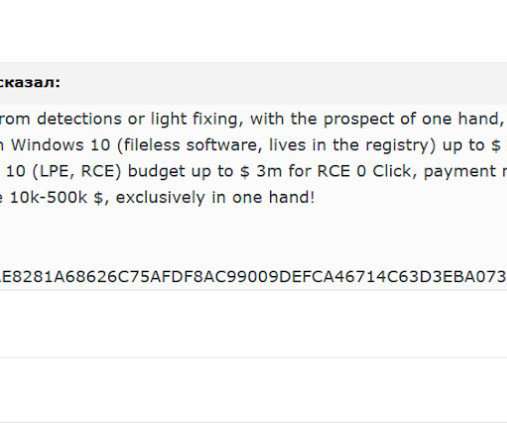
Security Affairs
NOVEMBER 17, 2021
Researchers detailed the multi-millionaire market of zero-day exploits, a parallel economy that is fueling the threat landscape. Researchers from Digital Shadows published an interesting research titled “ Vulnerability Intelligence: Do you know where your flaws are? ” reads the paper published by Digital Shadows experts.

IBM Big Data Hub
OCTOBER 3, 2023
But this growth in digital sales can come with a hefty price tag for retailers and consumer goods businesses: a much greater risk of data breaches. The Threat Intelligence Index also found that breaches against the retail and wholesale industry represented 8.7% With worldwide e-commerce sales totals expected to reach $8.1
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content