Recently patched Apple and Chrome zero-days exploited to infect devices in Egypt with Predator spyware
Security Affairs
SEPTEMBER 22, 2023
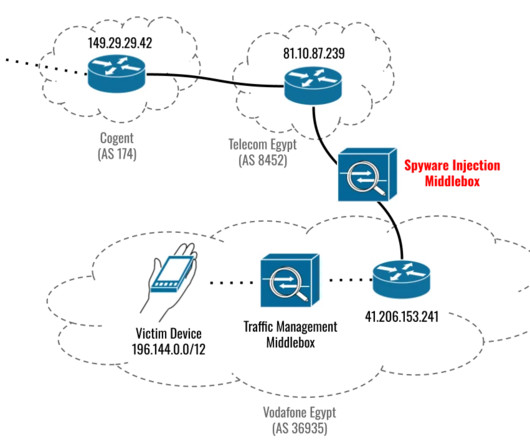
Citizen Lab and Google’s TAG revealed that the three recently patched Apple zero-days were used to install Cytrox Predator spyware. citizenlab in coordination with @Google ’s TAG team found that former Egyptian MP Ahmed Eltantawy was targeted with Cytrox’s #Predator #spyware through links sent via SMS and WhatsApp. .














































Let's personalize your content