MRO spare parts optimization
IBM Big Data Hub
JANUARY 25, 2024
Many managers in asset-intensive industries like energy, utilities or process manufacturing, perform a delicate high-wire act when managing inventory. Many asset-intensive businesses are prioritizing inventory optimization due to the pressures of complying with growing industry 4.0 What’s at stake?





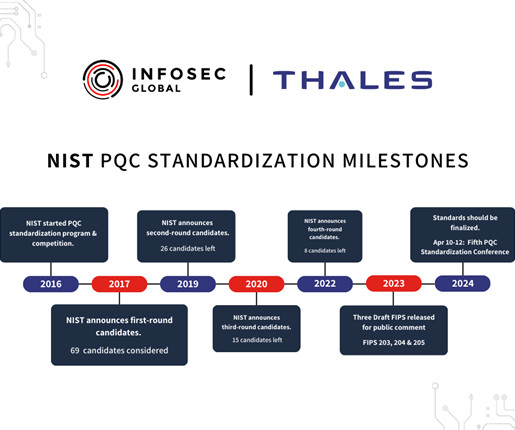


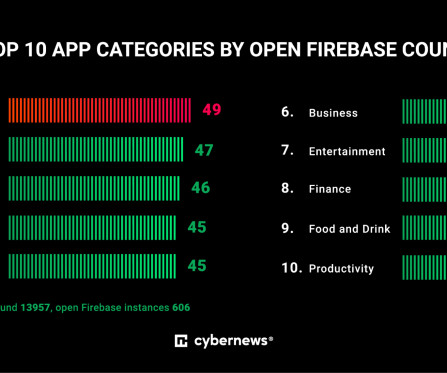











































Let's personalize your content