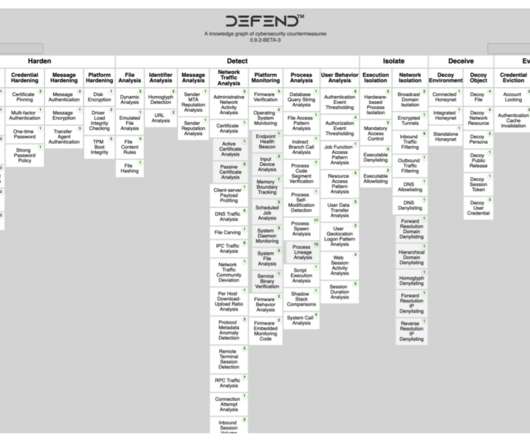
MITRE presents ATT&CK for ICS, a knowledge base for ICS
Security Affairs
JANUARY 8, 2020
MITRE announced the initial release of a version of its MITRE ATT&CK knowledge base that focuses on industrial control systems (ICS). Now the organization is going to propose a knowledge base that focused on ICS systems for its MITRE’s ATT&CK. ” reads the official page set up by MITRE.








































Let's personalize your content