How to make sure your cyber insurance policy pays out
IT Governance
JULY 15, 2019
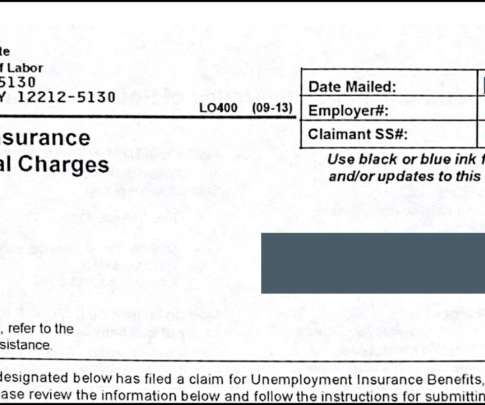
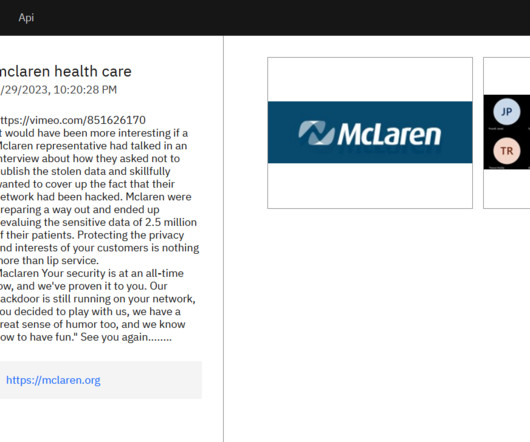
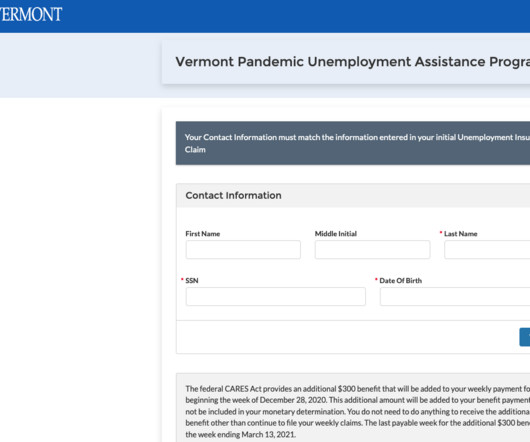
Cyber insurance is big business these days. With the ever-present danger of data breaches and cyber attacks, organisations must be sure that they have the financial backing to respond appropriately. The most common reasons that insurers reject cyber insurance claims are organisations’ failure to.












































Let's personalize your content