Researchers disclosed a remote code execution flaw in Fastjson Library
Security Affairs
JUNE 16, 2022
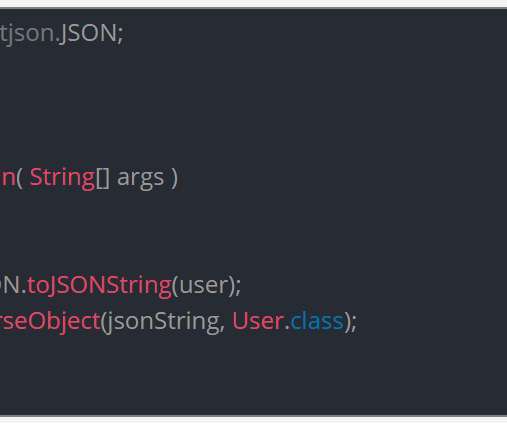
Researchers disclosed a remote code execution vulnerability, tracked as CVE-2022-25845, in the popular Fastjson library. Cybersecurity researchers from JFrog disclosed details of a now patched high-severity security vulnerability in the popular Fastjson library that could be potentially exploited to achieve remote code execution.






































Let's personalize your content