Operation Endgame
Troy Hunt
MAY 29, 2024
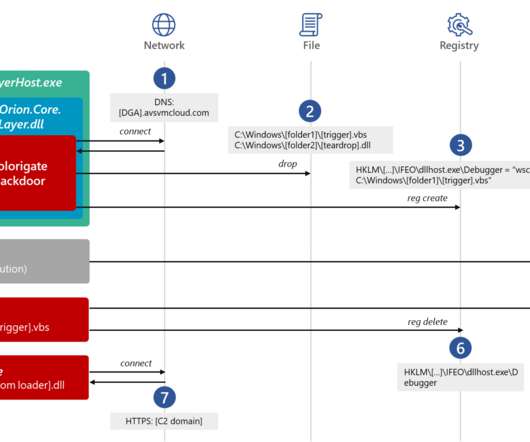
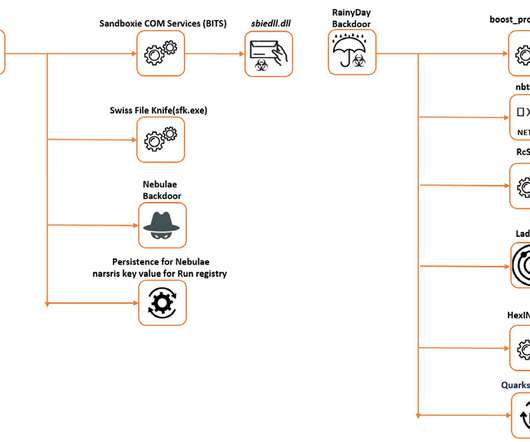
unique passwords provided by law enforcement agencies into Have I Been Pwned (HIBP) following botnet takedowns in a campaign they've coined Operation Endgame. The only data we've been provided with is email addresses and disassociated password hashes, that is they don't appear alongside a corresponding address.














































Let's personalize your content