New WastedLocker Variant Exploits Internet Explorer Flaws
Data Breach Today
MAY 20, 2021
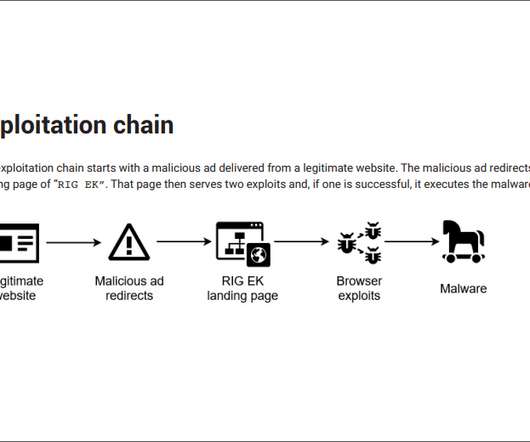
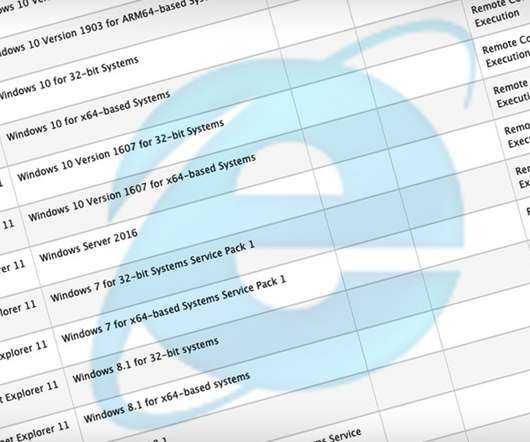
Bitdefender: Malware Loader Doesn't Contain Ransomware A new WastedLocker malware variant, dubbed WastedLoader, is exploiting two vulnerabilities in Internet Explorer to insert malicious advertisements into legitimate websites, the security firm Bitdefender reports.
















































Let's personalize your content