The proposed EU Cyber Resilience Act: what it is and how it may impact the supply chain
Data Protection Report
OCTOBER 17, 2022
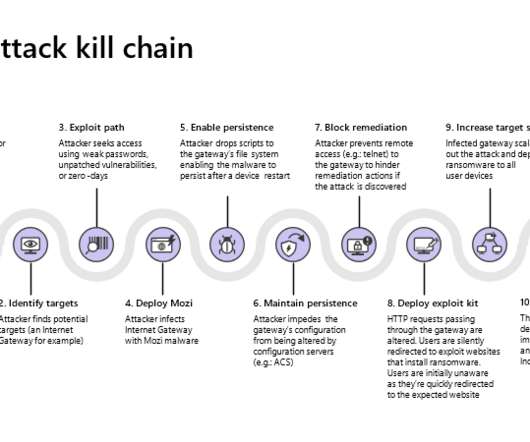
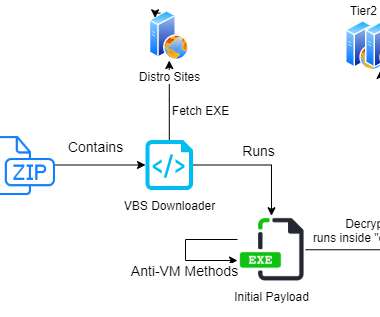
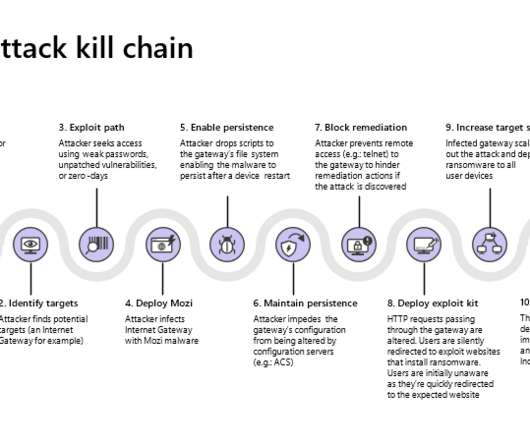
The CRA introduces common cybersecurity rules for manufacturers, developers and distributors of products with digital elements, covering both hardware and software. For example: “ products must protect the availability of essential functions, including the resilience against and mitigation of denial of service attacks”. .












































Let's personalize your content